‘Cacheout’ strikes Intel again- CPUs, VMs and Intel SGX affected
Intel processors have become a playing ground for attackers, started with Meltdown and Spectre, followed by Microarchitectural Data Sampling (MDS) now ‘Cacheout’ another speculative execution vulnerability fetching the data from Intel processors just like its predecessors but with more defense abilities.
What is Cacheout attack?
Cacheout is a speculative execution vulnerability in the modern Intel processors that were developed before October 2018. This attack was first discovered in Rogue In-Flight Data Load (RIDL) paper, by authors Stephan van Schaik, Cristiano Giuffrida, Alyssa Milburn, Pietro Frigo, Herbert Bos, Sebastian Österlund, and Herbert Bos. This attack extracts the data from the operating system using the buffer overflow attacks.
To explain clearly, our modern operating systems use Kernels and Stack Canaries, the former is used for randomizing the codes and data structures so the exact location of the data will not be easily revealed to the attacker, and the latter actually helps in creating a decoy for those data to detect attacks. However, with Cacheout both Kernels and Stack Canaries operation are brought to the day light and that’s how attackers can exploit the secured data inside the processors.
Cacheout is considered to be very critical by the researchers as it can bypass multiple boundaries, affecting hyper-threads, processors, virtual machines, user to kernel space, and even the Intel Security Guard Extensions (SGX).
The CVE for Cacheout attack is CVE-2020-0549: “L1D Eviction Sampling (L1Des) Leakage“, The CVE score is 6,5 medium.
How does Cacheout attack works?
Intel processors do contain a microarchitectural structures to store and process the data in transit. The attack allows a malicious application to push the processor data out from the L1-D cache to leaky buffers, then further extracting it outside of the victim’s system.
The below image shows how L1-D Cache, L2 Cache and Processor data read and write path.
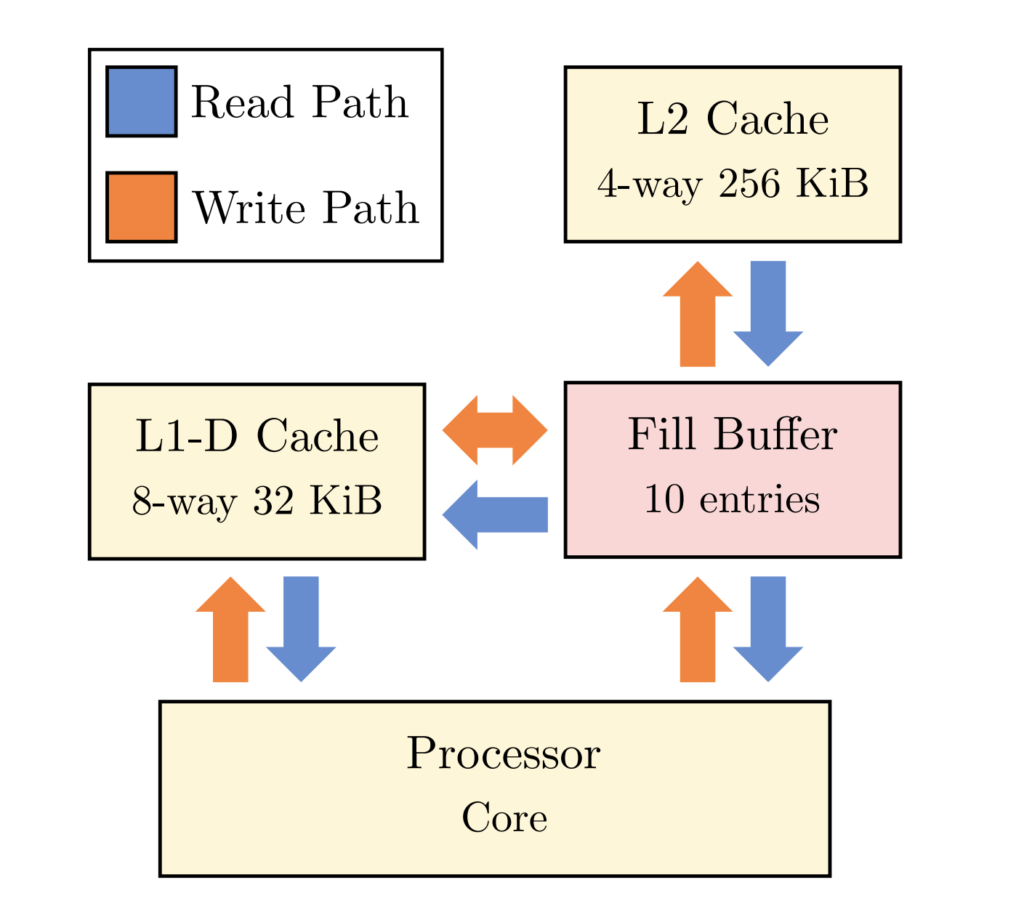
This attack creates contention at L1-D cache to force the data out of it, then moves the same to L2 cache, and then TSX Asynchronous Abort, and then broadcasting the data.
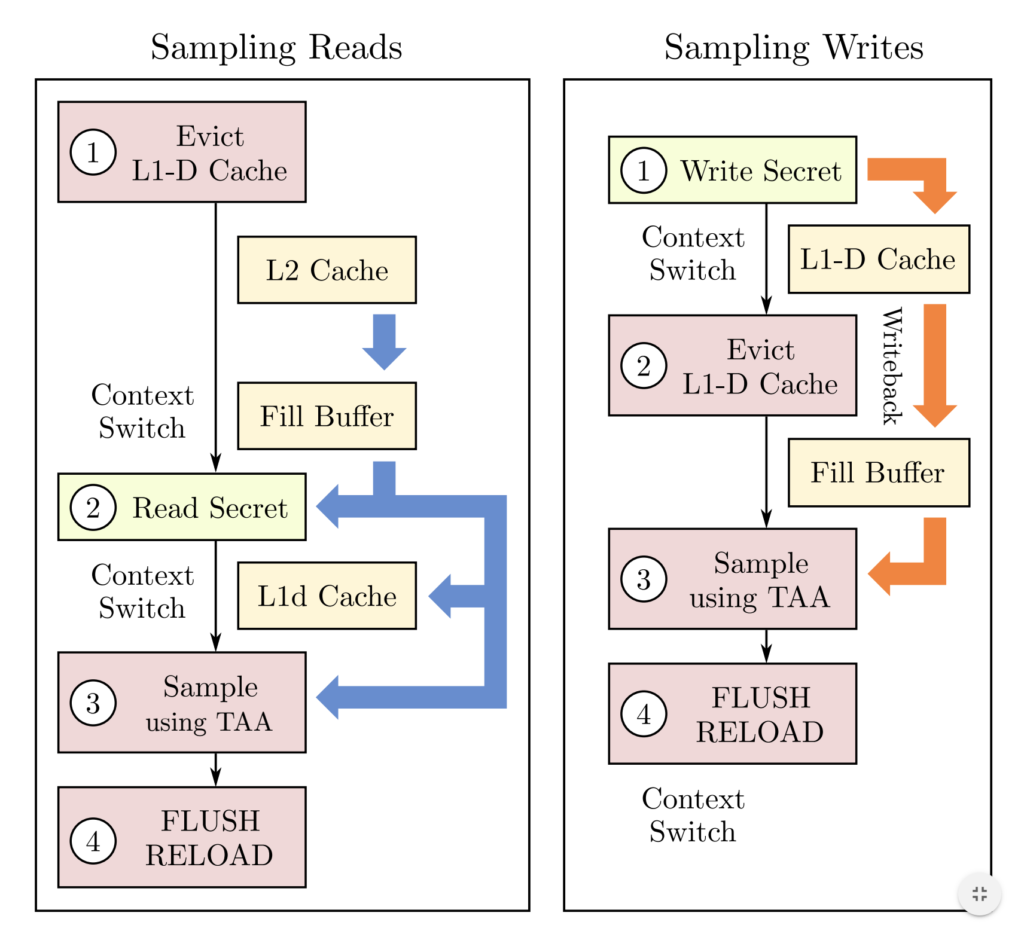
The below image shows the secret and evicted cache set,
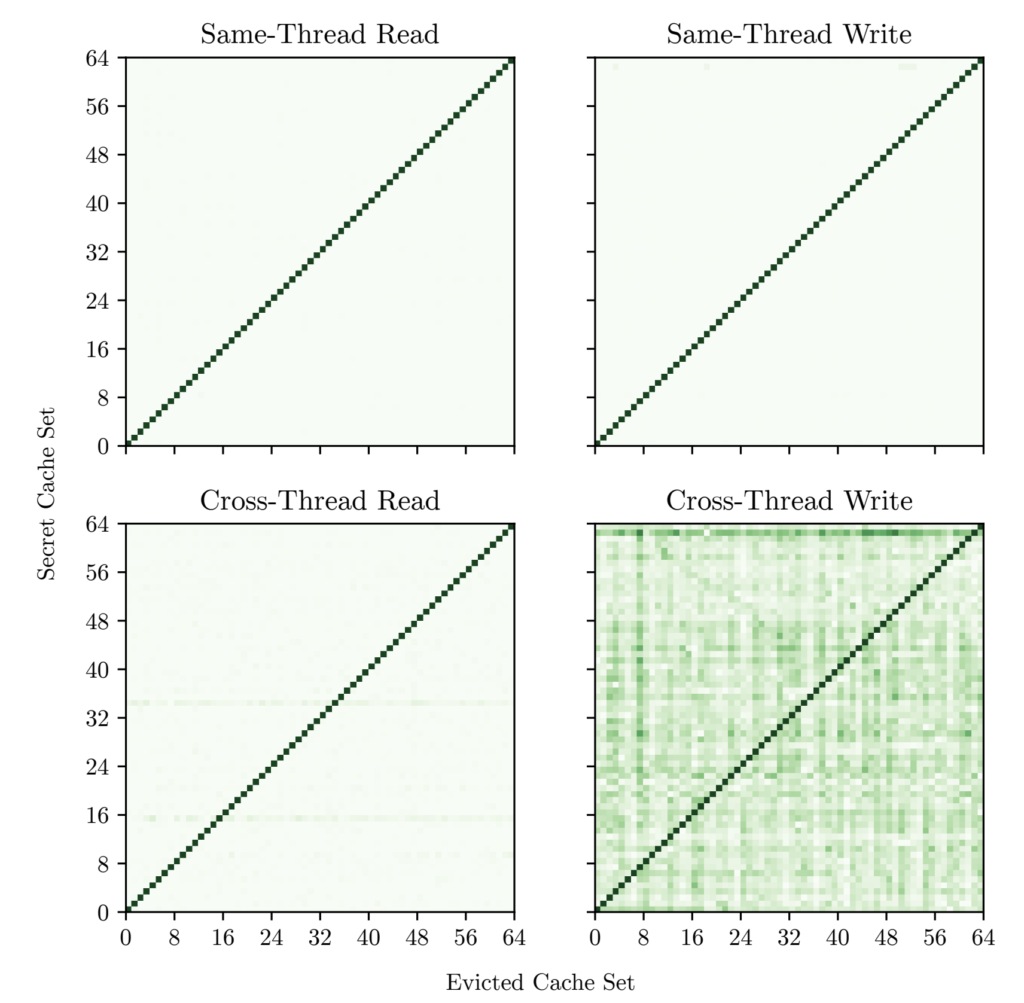
Other important points
- Anti-Virus can’t detect this bug, however it can in future once the binaries are circulated and another similar malware is detected exploiting the same vulnerability.
- The attack leaves no traces, so victims won’t even know whether they have been attacked.
- There are no wild reports of this attack yet.
- It can’t be exploited using browsers, they can’t expose the Intel TSX to Javascript.
How to fix Cacheout attack?
Intel has offered microcode updates, based on operating systems and hypervisors. Users can check for the Intel’s Security Advisory SA-00329 and their software based guidance for mitigating the attack.
Users are requested to keep their systems updated with the operating system and hypervisor updates. Please make sure, the patch revision number is greater or matching with the current revision number in the processors table.





