New Sugar ransomware demands low ransom targeting normal users

A new type of ransomware is found targeting individual user devices and not corporate networks, which is also demanding for low ransom. The ransomware is called Sugar Ransomware and was discovered by the Walmart Security Team.
What is Sugar Ransomware?
Sugar is a new Ransomwarew-as-a-Service threat established in November 2021 and is evolving gradually. The name Sugar denotes to the ‘sugarpanel[.]space’, an operation’s affiliate site as discovered by the Walmart team. This new Sugar ransomware isn’t targeting corporate network for major ransom but targets normal users and individuals for low ransom amount. It is also found to be targeting small and medium businesses.
However, as of now it is not clear how the ransomware is distributed and deployed into the victim devices.
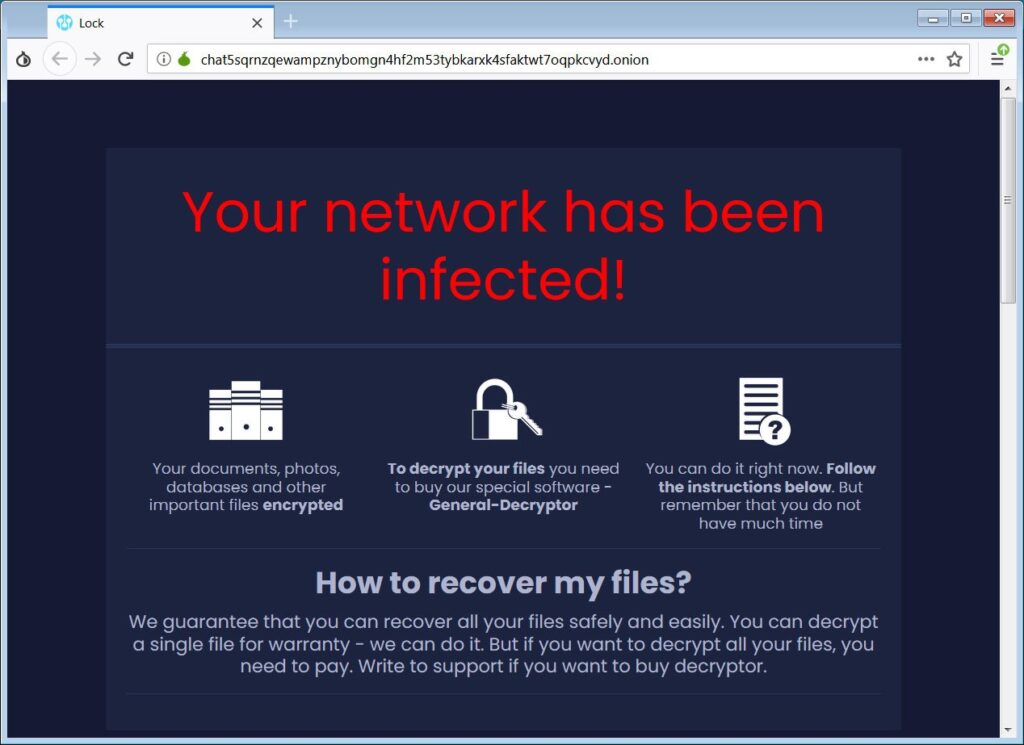
How does Sugar ransomware work?
After successful deployment, Sugar ransomware starts connecting to iplocation.com and whatismyipaddress.com to narrow down the IP address and location of the devices. Once the narrowing down of the device is done, it starts to download a 76MB file.
Post download of the file, the ransomware communicates with command and control server at 179.43.160.195, where it transmits and receives data about the attack. The ransomware also updates the status of the attack to the command and control server periodically.
The encryption of the files happens in the following folders,
Excluded folders:
\windows\
\DRIVERS\
\PerfLogs\
\temp\
\boot\
Excluded files:
BOOTNXT
bootmgr
pagefile
.exe
.dll
.sys
.lnk
.bat
.cmd
.ttf
.manifest
.ttc
.cat
.msi;As per Walmart research, the ransomware encrypts files using the SCOP encryption algorithm. The encrypted files have the extension.encoded01. The ransom notes contain information about the attack on the victim’s files with unique ID, and a link to Tor site with information on how to pay the ransom.
When the victim visits the Tor site they will be shown a bitcoin address for the ransom payment to be made with a chat section and option for decryptor.
The ransom demand was found to be only 0.00009921 bitcoins which is worth $4.01.
After testing the ransomware on a limited number of files, it is found that based on the count of encrypted files the ransom amount is decided. However, the ransomware doesn’t encrypt other files after its initial encryption. As of now, the weakness of the threat is yet to be discovered.
If you’re affected by the Sugar ransomware, please feel free to comment so others will have some light on how to handle the situation.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.





