Leaked Russian invasion plan map and new phishing campaign to gather info on Ukraine refugees

Anonymous shared a leaked document from Russian troops that depicts the war on Ukraine was approved on January 18, 2022 and the plan to invade Ukraine was put into place starting from February 20 to March 6, 2022.
The actual source and means the map was leaked is yet to be known, meanwhile this doesn’t seem like an act of Anonymous hackers though. Below are the leaked documents and maps that support the statement mentioned above.
Leaked document from Russian troops showing war against Ukraine was approved on 18th January, and initial plan to seize Ukraine starting 20th Feb to 06th March pic.twitter.com/4zsZD9i0R4
— Anonymous (@YourAnonNews) March 2, 2022
Namecheap announcement
On the other hand, Namecheap, US based domain register has announced that it will provide free domains and web hosting for anti-Putin sites. Meanwhile, it also requests its Russian clients to switch their web hosting and domain service provider due to the Russian invasion of Ukraine.
New phishing campaign targeting EU entities
With all that cyber war against Russia, it has to be mentioned that cyber attack is a double-sided sword and is targeting Ukraine and its supporters as well. A new state sponsored phishing campaign has been uncovered targeting European entities to obtain intelligence on Ukraine refugees and supply movement in the territory.
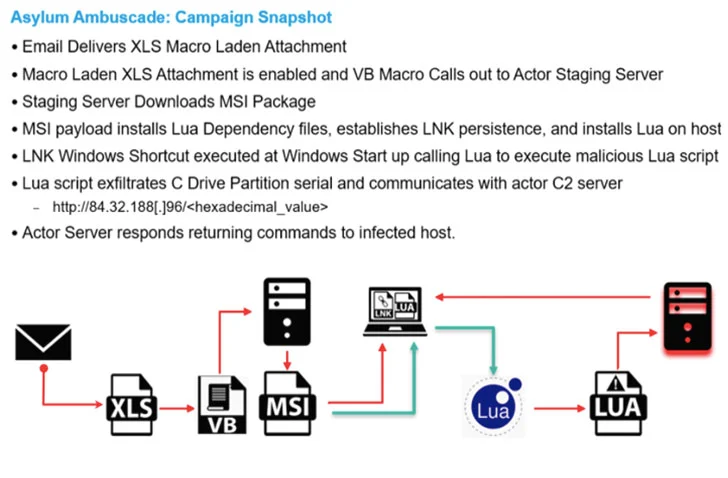
This campaign was first identified by Proofpoint and dubbed as Asylum Ambuscade, the emails were specially crafted for social engineering attacks around the emergency meeting of the NATO security council. Like any other phishing campaign, this one also comes with a macro which will download a malware called SunSeed to track the supply and management related movements in the area.
As per Proofpoint’s research and investigation this campaign is suspected to be launched by a Belarus hacker group called UNC1151 aka Ghostwriter.
Email security company Avanan mentioned that it had witnessed an eight-fold increase in email-borne attacks from Russia starting on February 27, targeting manufacturing, international shipping, and transportation companies located in the U.S. and Europe.
It is not even a week since the Russian invasion of Ukraine, and we already have seen several cyber attacks happening across the world and mostly with the Russia and Ukraine infrastructure. Though some battles are fought on the streets of Ukraine, some are fought on mind with laptops and desktops.
The attacks will only continue to rise unless the situation deescalates. Organizations across the world need to stay on high alert and ensure they are acting on security concerns to their best.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Twitter, and Reddit.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.








