ATW hackers linked with Anonymous breached into Russian Energy Giant

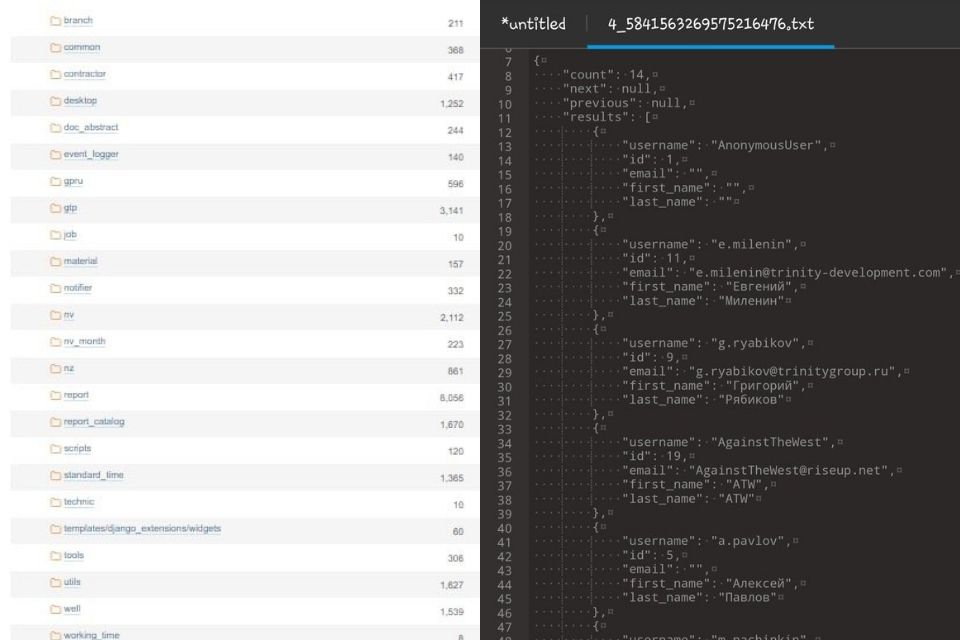
Anonymous linked hacking group AgainstTheWest (ATW hackers) has breached and leaked the database of Gazprom, a Russian majority state-owned multinational energy corporation. The leaked data includes details related to the company’s source code and WellPro projects.
JUST IN: #Anonymous-linked group ATW has successfully breached and leaked the database of Gazprom, a Russian majority state-owned multinational energy corporation. The leaked data includes information related to the company’s source code, and WellPro projects. #OpRussia #FCKPTN pic.twitter.com/KVJ5Je47Aj
— Anonymous TV(@YourAnonTV) March 4, 2022
ATW hackers, Anonymous and Ongoing CyberWar
Since the beginning of the Ukraine and Russian conflict, the internet is flooded with cyberattack news, especially after the Anonymous hackers declared Cyber War on Russia. Along with anonymous, multiple other hacking entities have come together to show their rage against Russian operation in Ukraine.
This includes IT army of Ukraine, the Network Battalion 65 (NB65), and the AgainstTheWest (ATW hackers). However, there are some entities working in support of Russia as well, like the Conti ransomware operators who pledged their allegiance to Russia. However, later Conti ransomware group’s internal chats and conversations were leaked by an insider, as the latter was in favor of Ukraine.
There are were two wipers, HermeticWiper and IsaacWiper malware that were deployed in Ukraine targeting government entities and key organizations since the beginning of the Russia operations in Ukraine.
The ATW hackers along with Anonymous has made the Grazprom data publicly available on the web.

We also did see how the NB65 claimed to have breached into the control center of the Russian Space Agency and the same was denied by the Director of the same organization, who said the systems were working as usual.
A few months back, hacking was a crime now it is being appreciated by many for the purpose it is being used for. We at The Cybersecurity Times advice organizations across the world to brace up and prepare for one long year of high-volume of sophisticated cyberattacks. Please ensure your networks and devices are equipped with the right security armor, and sustain your security best practices.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.








