A self-propagating malware campaign is cryptomining misconfigured docker containers

Docker containerization is under attack with a self-propagating cryptomining malware campaign that is targeting misconfigured Docker Daemon API ports. Gal Singer, a security researcher at AquaSec, has identified this campaign that has been there for months and is believed to be increasing in volume everyday. The researcher has stated that this campaign should be orchestrated by criminals who do have handful of resources and infrastructure to execute an attack at this level.
How does this self-propagating malware work
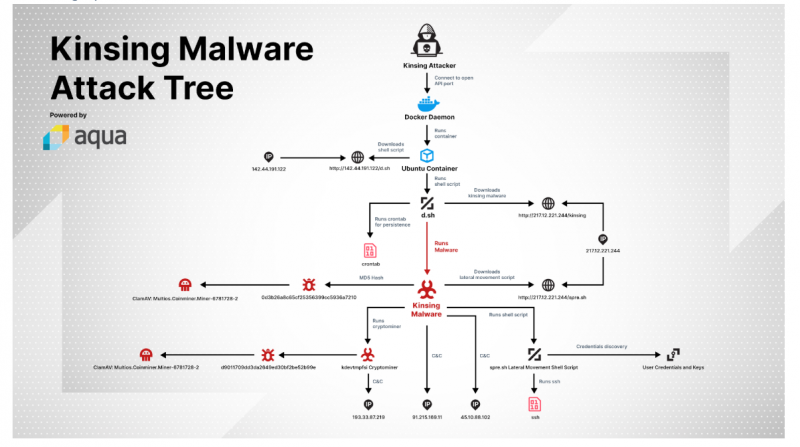
The attack begins like this, the attacker identifies a misconfigured Docker API port which is open to public internet, After accessing this open port, the attacker deploys a Ubuntu container and runs the same on the Docker connected to that open port. This container then fetches the kinsing malware using a command, which further downloads a cryptominer.
After all these initial build up, the kinsing malware self-propagates to other docker containers. This installer update to the docker container is updated using the shell script, which disables the security measures and also deletes the log files, and overwrites other malware or cryptominers that exists within. After completing this routine, the kinsing malware uses ‘crontab’ function to execute the same script every minute.
The kinsing malware is a Golang-based Linux binary, which in turn employs multiple libraries. The malware communicates with the C&C server using these libraries, which then gets it commands from that server to act as a dropper and execute scripts.
More about kinsing malware
Just like any other cryptominers, this campaign also includes a connection to the host and the mining process. The main difference in the campaign is the self-propagation technique that is employed by the attackers using the shell script.
The script identifies new targets using the data from ‘/.ssh/config,.bash_history,/.ssh/known_hosts’. With this information, the malware then propagates to the new host, through SSH, and then downloads the script and malware to propagate to the next host or containers. Based on the research by Singer, the C&C servers of this malware appears to be located in the eastern part of Europe, and the attackers have unique servers for each function of malware.
How to avoid such misconfigurations proactively
Docker is always known to have flaws, a source code was exposed due to the misconfigured Docker container registries, that belonged to retailers, news media and other organizations. Furthermore, in October around 2000 hosts of the unsecured Docker Engine were affected by cryptojacking worm.
The development, testing and security team have to work in coordination to avoid attacks like these, the hackers are becoming sophisticated day by day, and its important for the DevSecOps teams to build an effective Docker container security by locking them down appropriately based on the privileges. The cloud based resources had to be grouped together, and arranged in such a way that the most critical resources are protected the most, and appropriate privileges are defined. Vulnerability scanners can be employed to identify the loopholes and fix them before it is too late.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.





