ALPHV BlackCat Ransomware – The most sophisticated ransomware of 2021

A new ransomware operation is underway, it is named as the ALPHV aka BlackCat ransomware and is found to be the most sophisticated ransomware of 2021. It comes with high customization allowing attackers to manipulate victims with a new model of ransomware every time.
The ransomware exe is written in Rust that allows attackers to have better control as Rust provides better performance and memory safety for the malware.
MalwareHunterTeam was first to discover the new ransomware and published a tweet about the same. In the tweet, the researchers have claimed that there are already many victims for BlackCat and the malware UI looks like they are from 80s.
The ALPHV BlackCat ransomware was officially named as ALPHV and is now being actively marketed via Russian hacking forums. Just like other Ransomware-as-a-Service the BlackCat operators also recruit affiliates for corporate attacks and encryption.
Analyzed another sample of this not too long ago, but couldn't talk about it due to client confidentiality… uses AES128-CTR and RSA-2048, is secure. Filemarker 19 47 B7 4D at EOF and before the encrypted key, which is JSON with some settings. Very sophisticated ransomware.
— Michael Gillespie (@demonslay335) December 9, 2021
Features of ALPHV BlackCat ransomware
The BlackCat ransomware comes with some major features that makes it unique in the dark web market. This ransomware is a command line driven, manually operated, and highly customizable. It uses different encryption procedures, can laterally spread between devices, affect VMs and can erase ESXi snapshots thus preventing any recovery attempts.
The different type of encryption include, Full File Encryption, Fast Encryption for the first N Megabytes, DotPattern Encryption, Auto-encryption, Smart Pattern Encryption, ChaCha20 and AES.
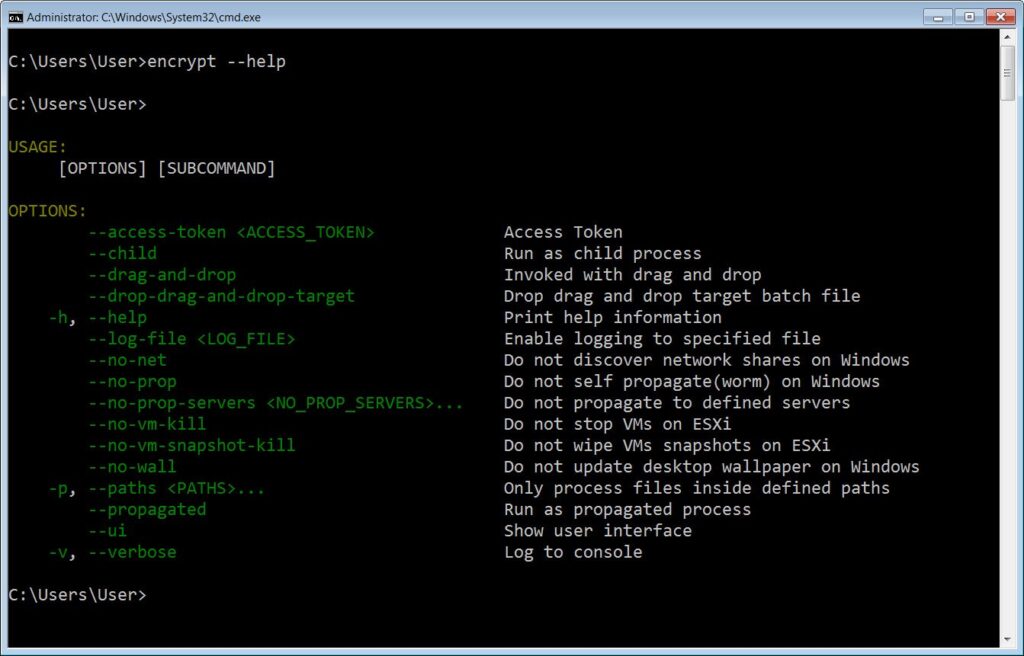
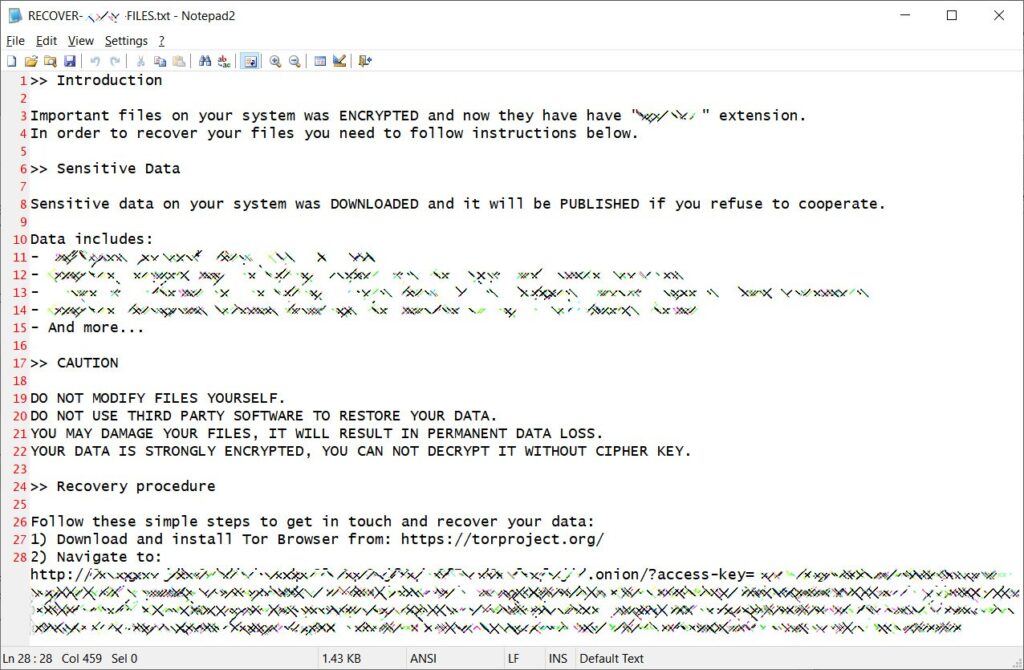
The attackers can even configure the ALPHV ransomware with domain credentials which can be used to encrypt other devices in the network, which later deploys ransomware by extracting the files. APLHV BlackCat uses the Windows Restart Manager API to close handle the process or shutdown Windows services. The ransom note for BlackCat comes as ‘RECOVER-[extension]-FILES.TXT’.
You can see the ransom note below,
More on BlackCat ransomware
BlackCat is found to be very sophisticated ransomware and could fill the empty space of BlackMatter and REvil ransomware operators after their recent shutdown. ALPHV uses a triple-extortion tactic as they steal the data before encrypting one and then threaten to publish the same if the ransom isn’t paid.
And the ransom demands ranges between $400,000 to $3 million payable via Bitcoin or Monero. So it is important for enterprises and business to keep their security up and active to avoid BlackCat into their network.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit. You can reach out to us via Twitter or Facebook, for any advertising requests.








