American enterprises are becoming victim to PwndLocker ransomware

Cyberattacks are escalating in 2020, especially in the United States. Even-though enterprises have been warned and a decent security policies are deployed, companies continue to become victim to ransomware threats. Cities and enterprises in the United States are falling to PwndLocker ransomware which is asking for ransoms around $650,000. This ransomware was first discovered by the end of 2019 and since then it has encrypted number of enterprises and has demanded ransom from $175,000 to$ 650,000 until now.
As per reports from Bleeping Computer, it seems the PwndLocker’s creators have stolen some files from the Lasalle’s county and had demanded for ransom, but that county had denied the payment of ransom. These attackers have also encrypted data from City of Novi Sad in Serbia.
How does PwndLocker ransomware work?
According to the reports produced by MalwareHunterTeam as shown below,
So, there’s a ransomware which we just call PwndLocker.
— MalwareHunterTeam (@malwrhunterteam) February 20, 2020
Not coded by skids…
Getting victims all over Earth…
Going for months, with like ~nothing about it public…
“The price depends on the network size, number of employess and annual revenue.”@demonslay335
cc @VK_Intel pic.twitter.com/u4arK4Hn7J
Once the ransomware enters the system using conventional phishing scams, it stops a substantial amount of windows and application services using the ‘net stop’ command for its uninterrupted process of encrypting the system.
Services like MQSQL, Veeam, Exchange, Acronis, Zoolz, Kaspersky, Sophos, Malwarebytes, McAfee and more. Apart from services, this malware also disables process like Firefox, Excel, Access, Word and other process based software, databases and backup applications. After it has prepared the system for the encryption, it begins its process and make sure it skips files that aren’t under its radar, for example: .exe, .dll, .cmd, .bat, etc.
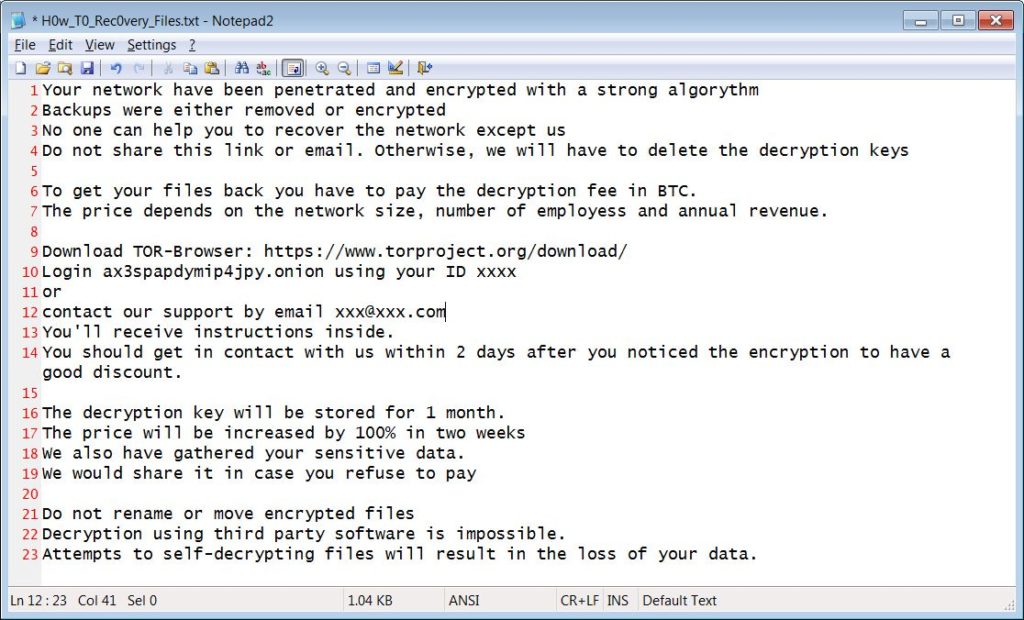
After encrypting the files in the targeted computer, this ransomware leaves .key and .pwnd extension on all the files. Displays a ransom note, allows victims to unlock two files for free and to access others they would need to pay the ransom.
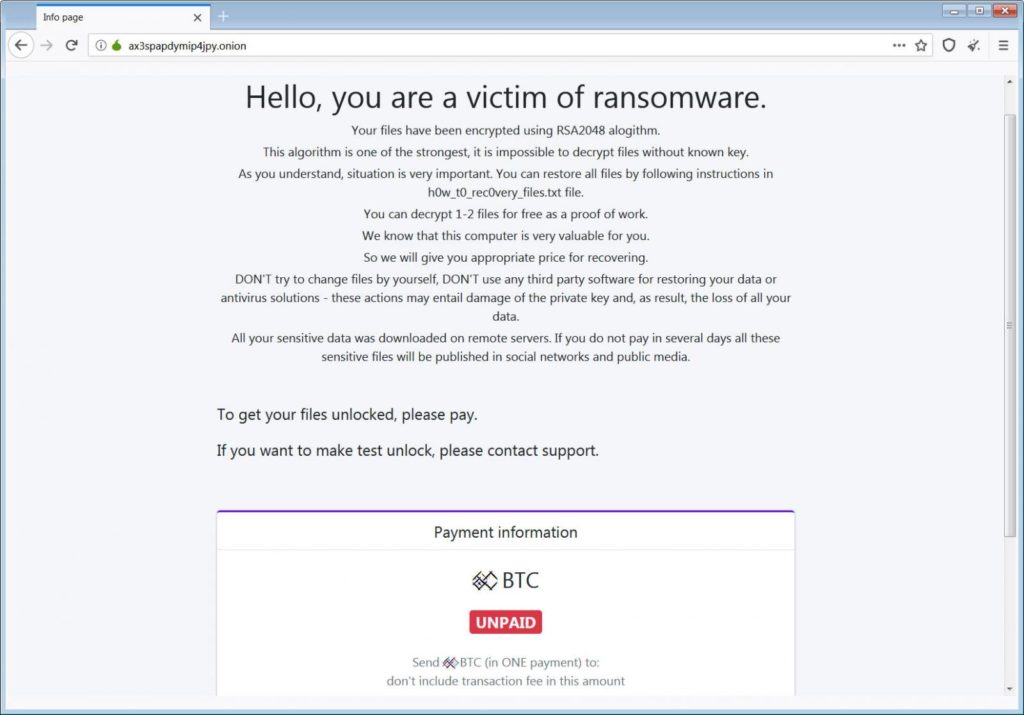
Proactive cybersecurity is the right way ahead against ransomware threats, but that can’t stand the threat if sufficient tools and awareness aren’t established already.
Subscribe to ‘The Cybersecurity Times’, for daily alerts on cyber events. You can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.





