Babuk Locker ransomware discovered in recent attacks

The Babuk Locker Operation used a leaked tool and the same tool is now being used by another threat group in an active campaign targeting worldwide victims. Babuk Locker was the ransomware operators behind the attack on Washington DC’s Metropolitan Police Department and the group then shutdown their operations with law enforcement department’s pressure on the group. However, they have now switched to a non-encrypting data extortion model named ‘Payload Bin’.
The Babuk Locker ransomware group was very active in the beginning of this year, targeting corporate networks and performing double-extortion attacks to steal their data.
Babuk Locker builder is reused by threat actors
A security researcher Kevin Beaumont identified that Babuk Locker is being reused in VirusTotal. And, it has been modified to make it look new by altering the ransom note with their new contact info, with the EXE that will create new encryptors and decryptors targeting VMware ESXi, NAS x86, and NAS ARM devices.
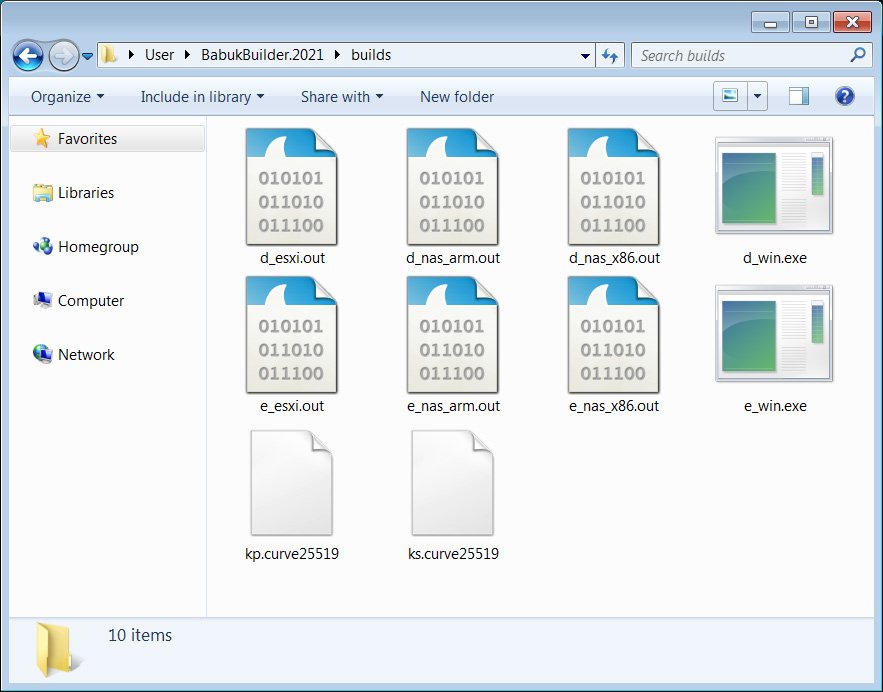
Babuk Locker ransomware in recent attacks
As soon as the leaked ransomware was reused a new ransomware campaign was launched and a Reddit user first reported it on Tuesday.
Also as per MalwareHunterTeam ID ransomware received a sharp hike in Babuk Locker submissions on June 29th and its spread across the world. All the ransom notes were directed to the same email address and this is how the hike looked like,
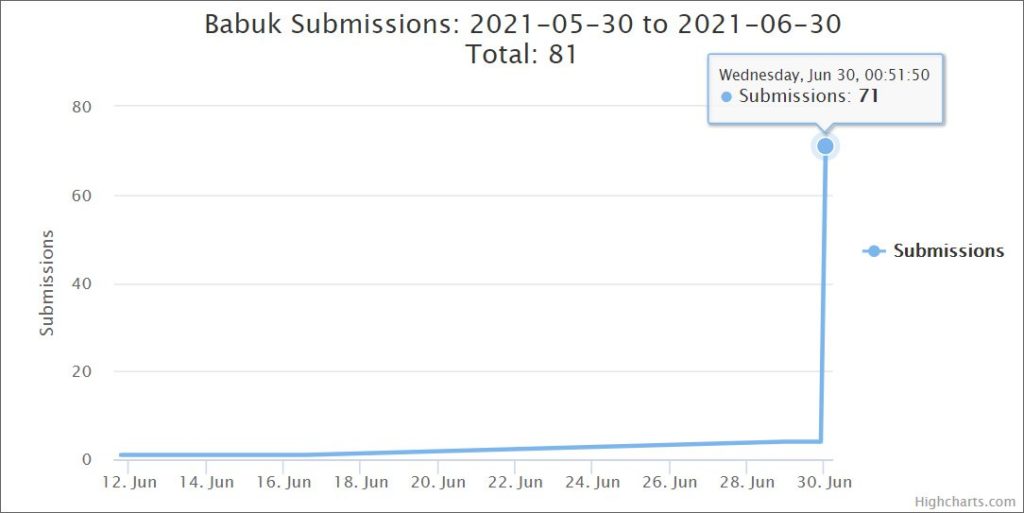
The ransomware adds on .babyk extension to the encrypted files and dropped a ransom note in ‘How to Restore Your File.txt’. However, the ransom requested is comparatively low to that of the original Babuk Locker ransomware attack that happened earlier in 2021. The original ransom note demanded for thousands of dollars while this new attack is demanding only 0.006 bitcoins, which is approximately $210 USD. Also, unlike the Tor payment site used for negotiations, this new attack is communicating using an email address as babukransom@tutanota.com for their negotiation.
Try these tools and drop your thoughts in the comments section. Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.





