Coronavirus themed cyberattacks continues to evolve: Malware and Booby-trapped URLs

Cyber industry is concerned about the new threats leveraging the corona virus anxiety. A few days back, The Cybersecurity Times published an article on the phishing campaign that clouted into people’s fear and made them open malicious attachments disguised to be corona-based advisories and precautions. This week, security professionals have identified substantial amount of new threats like booby-trapped URLs, coronavirus themed malware, and credential stuffing manoeuvres.

On March 3rd, researchers identified two new malware campaigns linked to the corona virus, first one spreads via phishing email to deploy Remcos RAT and malware, while the second one through Microsoft Office document dropping a backdoor into the victim’s computer.
The former disguises as a corona virus safety measures PDF, with a EXE file for Remcos RAT deployment which can run with a VBS file. This is found to be a sophisticated move, as the malware can clearly evade detection by firewalls as it establishes a TLS protection, thanks to Zlab-Yoroi Cybaze for sharing this with the cyber community.
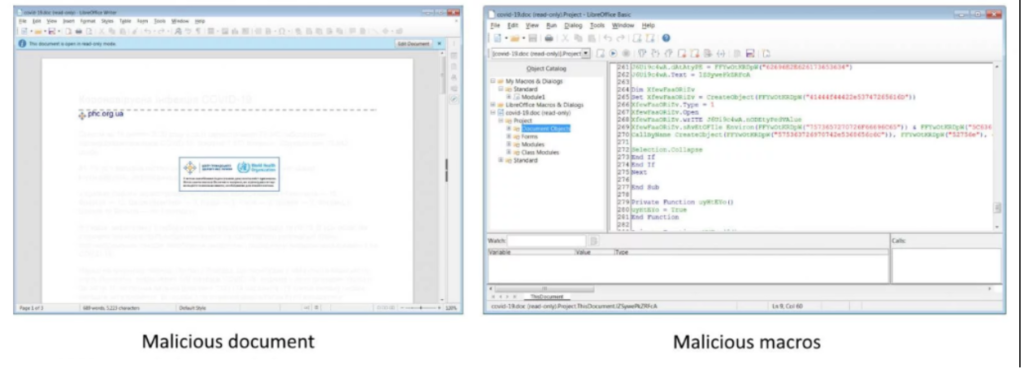
Once the systems are infected, the victims are asked to download and install two EXE files, and then the VBSscript is used for initiating the attack. On the other hand, MalwareHunterTeam, discovered a corona virus themed MS Office document which was pretended to be from Public Health Centre of Ukraine. This malicious document comes with macros that is designed to drop a backdoor into victim’s computers and can steal clipboard information, key-logging and even take screenshots of the infected computer.
Something even more threatening is, as per Check Point’s report there have been 4,000 corona virus related domains registered world wide. Among them, 3% of the domains are found to be malicious and 5% are suspicious. More fake emails pretending to be from Centre of Disease Control (CDC) are being broadcasted to take advantage of people’s anxiety and fear. A phished page is used for obtaining the credentials and when the user types in the password, the browser navigates the user to the legitimate CDC website keeping the attack absolutely sneaky.
How to stay safe against Corona Virus based cyber scams?
It’s surprising to see how attackers are taking advantage of such a concerning situation, this pandemic is already driving people crazy and employees have started working remotely. Cyberthreats like corona virus themed malware, booby-trapped URLs, back doors, and phishing campaigns are going to be around for a while, and users are advised to check their emails with caution, do not download unknown attachments from anonymous senders, and always look for pushing content in the emails.
While IT departments need to force strong data security policies like browser isolation, automated patch management, security information and event management (SIEM), log management, user and entity behavior analytics (UEBA), blacklisting and whitelisting applications, email security management, content management, device management and more to keep their employees, clients and partners secured and safe from corona virus themed cyberattacks.
Subscribe to ‘The Cybersecurity Times’, for daily alerts on cyber events. You can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.





