COVID passport apps puts users privacy and their personal data at risk

The Digital Vaccination Applications that are commonly used as safe passes and travel passports are exhibiting behavior that could put users’ privacy at risk. The risks are substantial as these COVID passport apps are used by large population across the world, and are becoming a target beacon for hackers.
COVID passport apps and their security posture
The COVID Passport apps does store a user’s COVID-19 vaccination certificate which includes name, ID number, date of birth, vaccination date, vaccine name and other personally identifiable information (PII) that is encoded in a QR code inside the app. With this QR code the users are accessed for proof of vaccination when they enter certain buildings or travel from one country/city to another.
Though these software is offered by governments and health departments of a nation, they are developed by external developers who could be on a contract to develop the app for public usage.
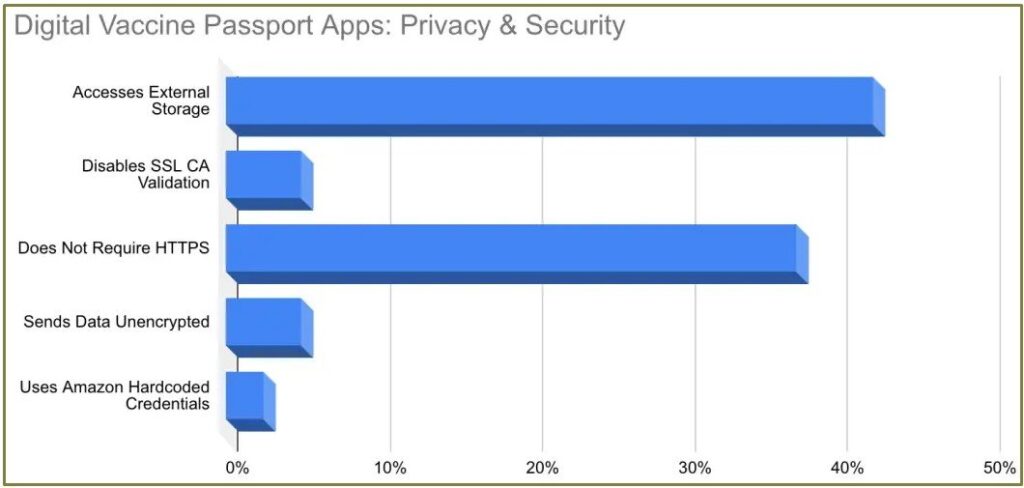
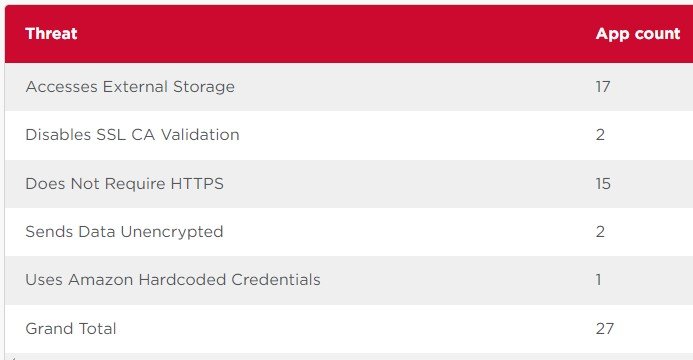
After some detailed analysis on 40 COVID passport apps and ten validation applications, Symantec team found that 27 of the apps suffer from some of the following privacy and security loopholes.
COVID passport apps’ QR codes aren’t encrypted
The first issue as per Symantec report is that most of these COVID passport apps are generating a QR code that is just encoded and not encrypted. Encode means data conversion, likewise in the vaccination QR code case, the health data is converted to a digital format that would be easy to scan and process.
However, encryption is the process of transforming data into non-readable format using cryptographic algorithms which can be deciphered only using the authorized entities who hold the decryption keys.
Since the QR codes rely on encoding and not encryption, they can be easily decoded and then the sensitive data of the users can be manipulated by any threat actors.
Non-HTTPS health data transfer
The health data transferred from the cloud storage service does not require an HTTPS connection in 38% of the cases, which makes users data even more vulnerable to man-in-the-middle (MITM) attacks.
External storage permission on Android
The third issue is the data is being stored external with access permission on Android. This is a risky approval as it can give unconditional access and privilege to the device’s locally stored files. This storage issue was identified in 17/40 apps that is 43% in total.
Adding to the above three security concerns the hard-coded cloud service credentials, absence of SSL CA validation also pushes users data on high risk zone.
How can you secure your COVID Passport Apps and its PII data
If you’re entitled to use the Digital Vaccination Passport App, please avoid third-party and external wallets from unknown vendors. Better to stick with the firms that vet them more vigorously, example Google Wallet and Apple Health.
While installing these applications, please ensure you think twice and deny unnecessary permissions without affecting the core functionality of the device.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.








