DarkWatchman malware is sneaky and hides in the Windows Registry

Technical Researchers from Prevailion have discovered a new malware called ‘DarkWatchman’ that is highly-capable of JavaScript RAT along with a C# keylogger. This new malware is used by Russian actors targeting Russian entities. This malware was first discovered in November and was distributed using phishing campaigns.
The Modus Operandi of DarkWarchman malware
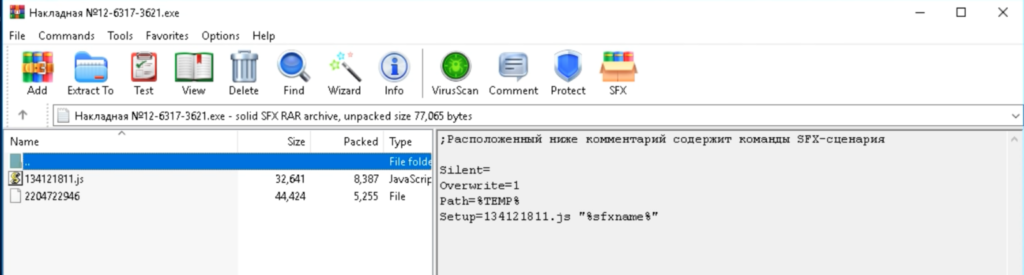
The phishing emails contained a ZIP document which had an EXE file but impersonated as a text document. This EXE file can auto-install itself and deploy the RAT and Keylogger. Once the victim opens the ZIP document, a popup message will be shown, displaying ‘Unknown Format’, while the malware is silently installed in the background.
The JavaScript RAT file is only 32 kb in size and thus a very light weight malware. The DarkWatchman malware uses the binaries and scripts to execute the stealthy mode data transfer between its modules. The malware also uses the Windows Registry fileless storage mechanism for the keylogger. There will be a scheduled task created to initiate the RAT every time without storing the keylogger in the desk.
DarkWatchmen malware executes a PowerShell Script which will execute the .NET CSC.exe command and deploys it into the memory.
The Prevailion researchers said the following regarding they Keylogger and RAT combo,
“The keylogger is distributed as obfuscated C# source code that is processed and stored in the registry as a Base64-encoded PowerShell command. When the RAT is launched, it executes this PowerShell script which, in turn, compiles the keylogger (using CSC) and executes it. The keylogger itself does not communicate with the C2 or write to disk. Instead, it writes its keylog to a registry key that it uses as a buffer. During its operation, the RAT scrapes and clears this buffer before transmitting the logged keystrokes to the C2 server.”

Also the registry is used more than just hiding the exe file by acting as a temporary location by holding the stolen information until its been exported to the C2. The DarkWatchman malware uses domain generation algorithms (DGA) to generate 500 domains everyday.
DarkWatchman malware comes with several threats,
- Capable of loading DLL files
- Execute commands
- Execute EXE files
- Execute WSH commands
- Export files to C2 server
- Remote control and update over RAT and Keylogger
- DGA for C2 resilience
- Overrides admin permissions by deleting shadow copies using vssadmin.exe
DarkWatchman Malware and the ransomware suspicion
Prevailion mentions that DarkWatchman malware could be orchestrated by ransomware operators as they may need a sneaky assistance for their bigger missions. Since DarkWatchman can load more payloads and be used for ransomware deployments as well. With DarkWatchman malware ransomware attacks could become more sophisticated and it will be challenging to narrow down the suspects unless they make the claim themselves.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.





