DopplePaymer Ransomware launched a website called ‘Dopple Leaks’ to disclose the encrypted data.

Ransomware has been known for causing havoc to enterprises by encrypting data and asking for a ransom, however in recent times, Ransomware creators have taken things seriously by publishing the victim’s data on a hosted website. Maze ransomware first initiated this publishing behavior, when its victims denied to pay the ransom. Now DopplePaymer Ransomware creators have published a new website called ‘Dopple Leaks’ were it has disclosed the encrypted data of few companies that it had infected.
With DopplePaymer following up with Maze’s tactics of exposing victim’s data, Sodinokibi, and Nemty have also stated that they would probably follow the same in future.
DopplePaymer is an enterprise targeted malware that infiltrates networks, gain access to administrator credentials and eventually spread to the network devices to break the productivity, integrity and confidentiality of the enterprise. Below is the site that creators of DopplePaymer had created, the Dopple leaks.
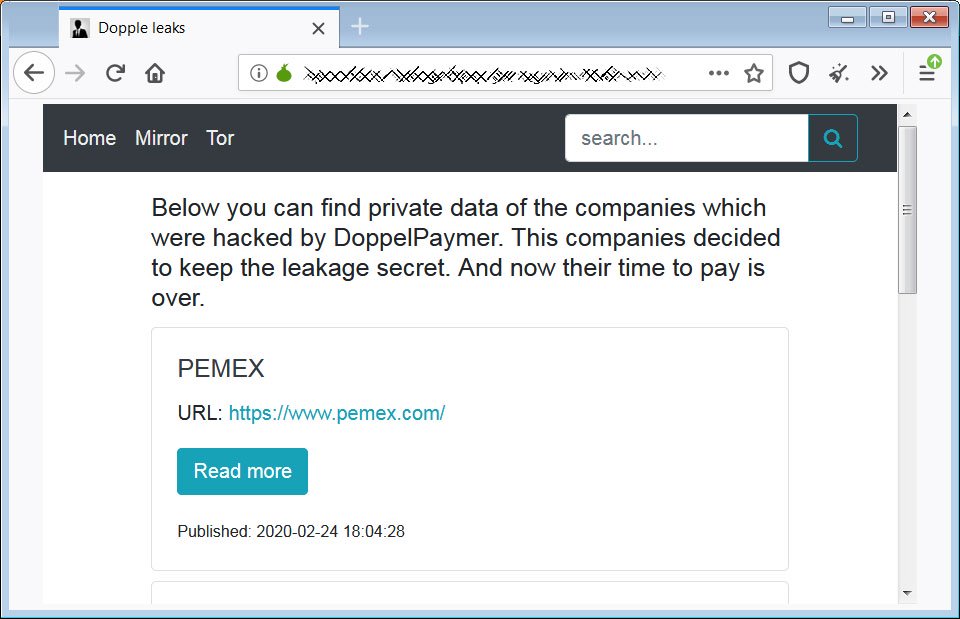
As per DopplePaymer ransomware creators, four companies that become victim to their attack and had not paid the ransom yet.
- Pemex, state-owned oil company in Mexico that became victim to DopplePaymer in Nov 10th, 2019.
- A logistic company from South Africa became a victim on Jan 20th, 2020.
- A French cloud hosting and telecommunications company and
- A US based merchant account company.
Ransomware can now encrypt, demand ransom and publish data
Ransomware is no longer just an encrypting malware that demands for ransom, with Maze and DopplePaymer ransomware creators publishing victim’s data, this is now threatening companies for data breaches and could even result in penalization from data law regulatory organizations.
Enterprises are requested to keep their proactive and reactive security up 24/7 and if in case they became victim to a cyberattack and could lose employees, vendor, client or personal data of any entity it is always good to disclose the attack, this way they can at least caution the affected entities.
Subscribe to ‘The Cybersecurity Times’, for daily alerts on cyber events. You can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.








