

Industrial cybersecurity company Dragos recently revealed a significant “cybersecurity event” in which a notorious cybercrime gang attempted to breach their defenses and infiltrate their internal network to encrypt devices.
Although Dragos asserts that the threat actors were unsuccessful in breaching their network or cybersecurity platform, they were able to gain access to the company’s SharePoint cloud service and contract management system.
This incident highlights the growing persistence of cybercriminals and the importance of robust security measures.
During the attempted breach, the criminal group exploited the personal email account of a newly hired sales employee, leveraging their personal information to impersonate a Dragos employee and initiate initial steps in the employee onboarding process.

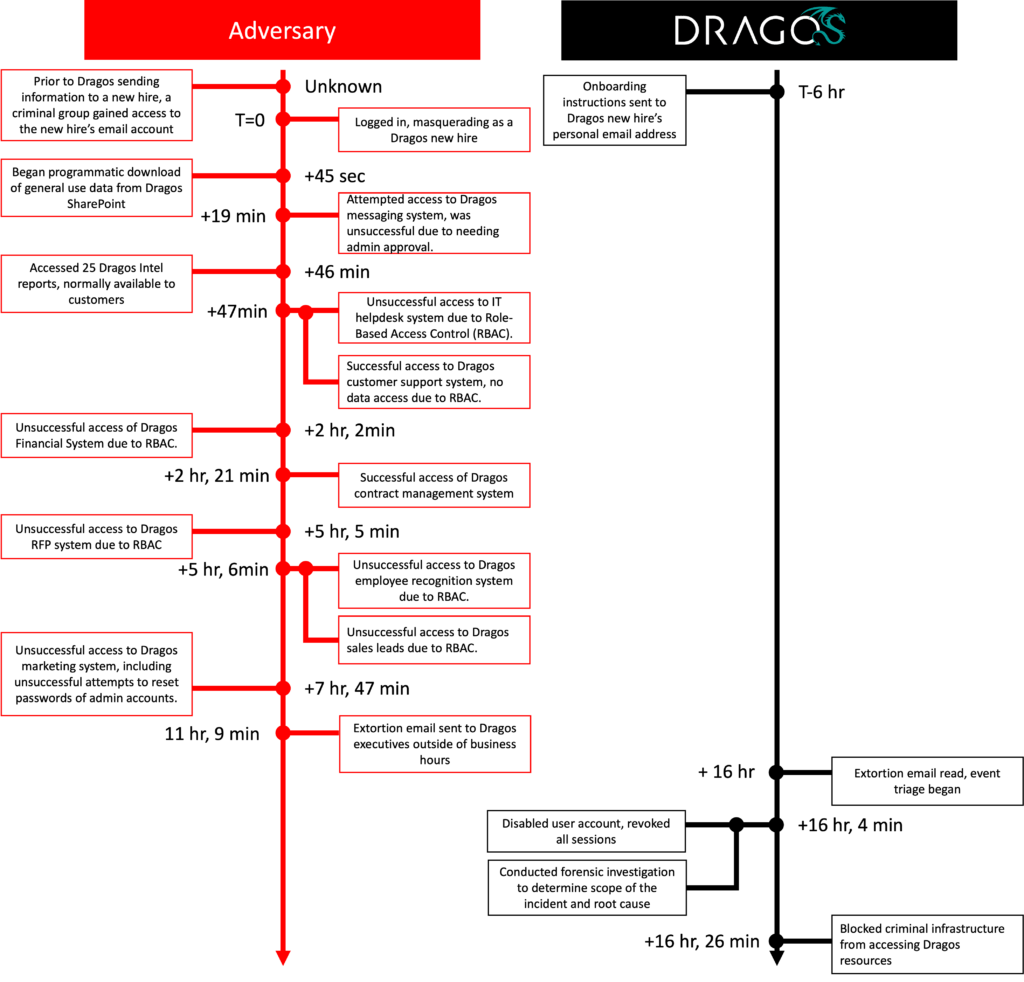
The cybercriminals breached Dragos’ SharePoint cloud platform and proceeded to download “general use data” while also accessing 25 intelligence reports typically restricted to customers.
Despite the 16-hour window in which the attackers had access to the compromised account, they failed to infiltrate several critical Dragos systems.
Systems such as messaging, IT helpdesk, financial, request for proposal (RFP), employee recognition, and marketing systems remained secure due to robust role-based access control (RBAC) rules.
Eleven hours into the attack, the cybercriminals sent an extortion email to Dragos executives, which went unnoticed for five hours as it was sent outside business hours.
Once the message was discovered, Dragos swiftly disabled the compromised user account, terminated all active sessions, and blocked the attackers’ infrastructure from accessing company resources.
Through these layered security controls, Dragos successfully thwarted the threat actors’ primary objective of deploying ransomware and impeded their lateral movement, privilege escalation, and infrastructure modifications.
In an attempt to extort the company, the cybercrime group threatened to publicly disclose the incident by reaching out to Dragos executives, senior employees, and their family members through public contacts and personal emails.
Despite the potential loss and public disclosure of data resulting from their decision not to pay the extortion demand, Dragos remains confident that the event has been contained, emphasizing that the incident is still under investigation.
One of the IP addresses associated with the attack (144.202.42[.]216) has previously been linked to SystemBC malware and Cobalt Strike, commonly utilized by ransomware gangs for remote access to compromised systems.
The presence of this IP address in recent BlackBasta ransomware attacks provides some leads in identifying the potential suspects. However, determining the exact threat actor behind the attack remains challenging due to the multiple ransomware gangs known to employ SystemBC.
Dragos continues to collaborate with external incident response firms and their analysts to investigate the cybercrime group responsible for this incident.
As the investigation progresses, Dragos aims to provide further details on the attackers’ identity and intentions.
The company’s commitment to strengthening cybersecurity measures underscores the importance of constant vigilance in the face of evolving cyber threats
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…