Dridex malware is sending fake termination emails to employees

A phishing campaign is ongoing and deploying a new malware called Dridex. This campaign sends fake employee termination emails so the victims will fall for the bait and open the email with a malicious excel file which when opened mocks the victims with season greetings.
Dridex is a banking malware that is being spread to steal banking credentials. The threat actors later enhanced the malware with multiple modules with advanced malicious intents, like payload deployment capabilities, remote access, lateral distribution perks and more.
Dridex malware was created by Evil Corp which were the ones behind DoppelPaymer, WastedLocker and BitPaymer ransomware, which brings the suspicion that Dridex malware could lead to ransomware attacks later.
A deeper analysis on Dridex malware
Dridex malware has already been part of several phishing campaigns in recent weeks where the email is addressed to mock researchers with a racist and antisemitic approach.

TheAnalyst, a security researcher has identified this Dridex malware with its fake employee termination emails. The emails are sent with a subject line ‘Employee Termination’ with the content showing the end date of employment by Dec 24th, 2021. The email has an Excel Sheet with name ‘TermLetter.xls’.
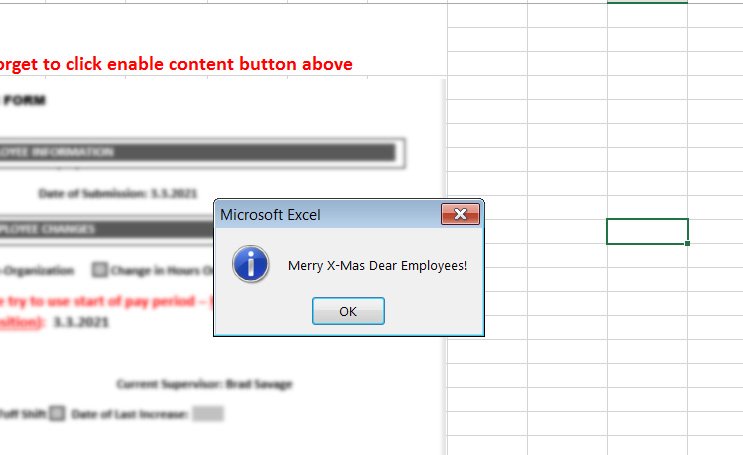
Once the file is opened, it asks for a password with request to enable content to view the file. Once the victim enable the content option, a ‘Merry-X-Mas Dear Employees’ greeting is displayed, while the macros are being executed in the background.
This macros will execute a HTA file with malicious VBScript that will download the Dridex Malware from the Discord with a file name called ‘jesusismyfriend.bin’. After successful installation of the Dridex malware, multiple other malware are downloaded for performing further infiltration into the victims network.
How to stay vigilant against Dridex malware?
Always check your email sender, subject line, and the domain name of the sender email address. If you see any termination emails be extra cautious and check with your HR department and do not ever open the suspicious mail unless otherwise advised by your IT or HR department directly.
To all the system and network administrators out there, we are close to the holidays, please boost up your network security by double checking malware threats and alert your employees about such campaigns.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.








