Earth Lusca group targets cryptocurrency and government bodies

Cybersecurity researchers have discovered a China based cyber-espionage operators that is spying on targets and is deploying attacks for financial benefits. The group was identified to be Earth Lusca and has been spying targets for more than two years now.
The targeted bodies include,
- Government organizations in Thailand, Vietnam, UAE, Mongolia, Nigeria, Taiwan and Philippines.
- Media and News bodies in Japan, France, Hong Kong, Australia and Hong Kong.
- Educational institutions in Hong Kong, Japan, France and Taiwan.
- Covid-19 research entities in US
- Human rights political organizations in Hong Kong.
- Telecom firms in Nepal.
- Mainland China and the religious movements associated with it.
The primary intention is to collect intelligence from these entities. However, as per the report from Trend Micro the group has also been involved in orchestrated attacks against gambling companies, cryptocurrency platforms, and other bodies from where the financial benefits are reaped.
Earth Lusca or APT41?
The government espionage group involved in financially motivated attacks has become a pattern lately. iran based threat actors have been breaching VPN devices around the world, targeting important entities for spying, data extraction and selling the info on the dark web.
However, in the case of North Korean actors they are being sponsored by the state to attack bodies and raise money for the Pyongyang regime to improve the economy that has been down for a long time. This dual behavior of collecting info and gaining financial benefits is already reported by FireEye as Double Dragon.
The Earth Lusca Group and APT41 seem to have a lot in common including the attack vector and tactics, thus making APT41 the major threat actor in the world right now.
Modus Operandi of Earth Lusca Group
Trend Micro’s report shows that the Earth Lusca Group primarily uses three methods to attack an entity,
- Leveraging and exploiting unpatched vulnerabilities in public facing servers and web apps.
- Orchestrating spear phishing attacks with links to nefarious websites.
- Watering hole attacks to lure visitors and deploy malware via the websites.
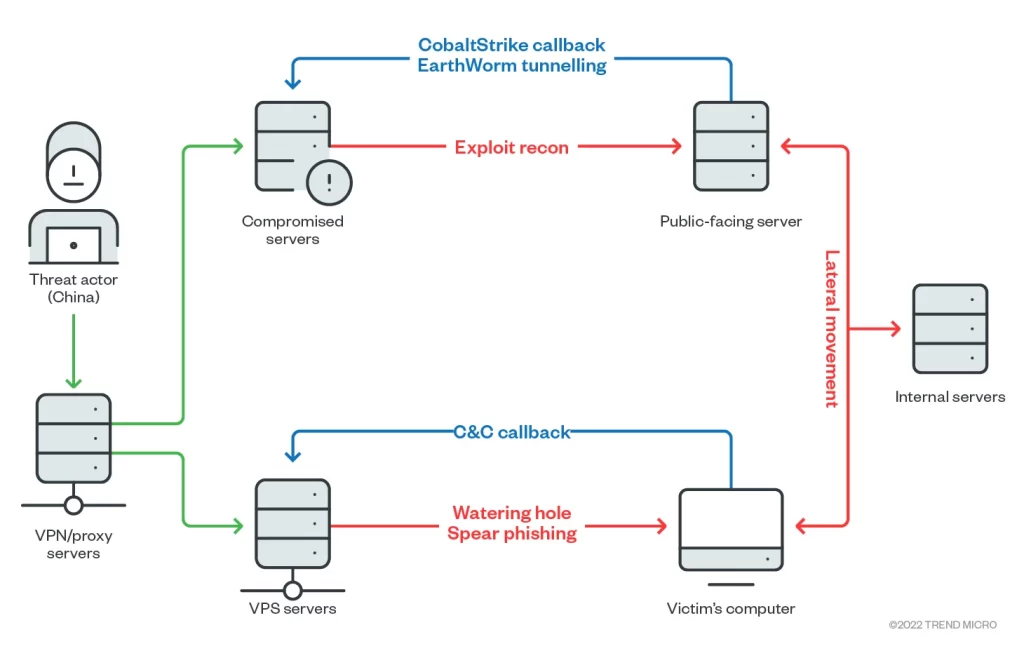
The researchers have seen Cobalt Strike as the common maneuver to infect hosts by deploying it on the target environment. Cobalt Strike is often used by security professionals to simulate attacks but recently been used by threat actors for their modus operandi.
Once the Earth Lusca actors are over the preliminary steps, they start deploying other payloads on the devices. Which includes,
- Winnti backdoor
- Doraemon backdoor
- Behinder Web shell
- AntSowrd web shell
- FunnySwitch backdoor
- ShadowPad backdoor
- Cryptominers
The cryptominer deployment is a brilliant maneuver to divert the detection to monetary benefits and hide the fact that Earth Lusca is behind the intelligence and data, the cyber-espionage campaign will be complete stealth while the cryptominer will be the dummy that gets caught instead.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.





