Email Hacking: How Cybercriminals Can Steal Your Identity

Hacking Email: A Hacker’s Perspective” – Learn how hackers exploit your email and steal personal data. Protect yourself with best practices.
Greetings, Cybersecurity Community! Today, we are going to delve into the world of email hacking, which is one of the easiest and most effective ways to gain access to a person’s personal information.
Email hacking is an essential skill that every hacker should master, as it can provide a wealth of valuable information that can be used for nefarious purposes. So, let’s get started!
Hacking Email: How Hackers Get Your Email?
The first step in hacking email is to get your hands on the email address that you want to target. This can be done in a variety of ways, such as:
- Social engineering: Hackers can use social engineering techniques to trick people into giving them their email addresses. For example, they may pose as a customer service representative and ask for the person’s email address to resolve an issue.
- Public records: Email addresses can be found in public records, such as online directories or social media profiles.
- Data breaches: Hackers can obtain email addresses from data breaches, such as the recent Facebook and LinkedIn breaches.
- Brute force attacks: Hackers can use brute force attacks to guess email addresses by using common names, words, and phrases.
Why Hacking Email is the Jackpot?
Now that we have your email address, let’s discuss why hackers are so interested in it. Your email address can provide a wealth of information that can be used for various purposes, such as:
- Phishing attacks: Hackers can use your email address to send phishing emails, which are designed to trick you into providing sensitive information, such as passwords and credit card numbers.
- Identity theft: Your email address can be used to steal your identity, as it is often linked to other accounts, such as social media, banking, and shopping websites.
- Spamming: Hackers can use your email address to send spam emails, which can clog up your inbox and slow down your computer.
- Ransomware attacks: Hackers can use your email address to launch ransomware attacks, which can lock you out of your computer until you pay a ransom.
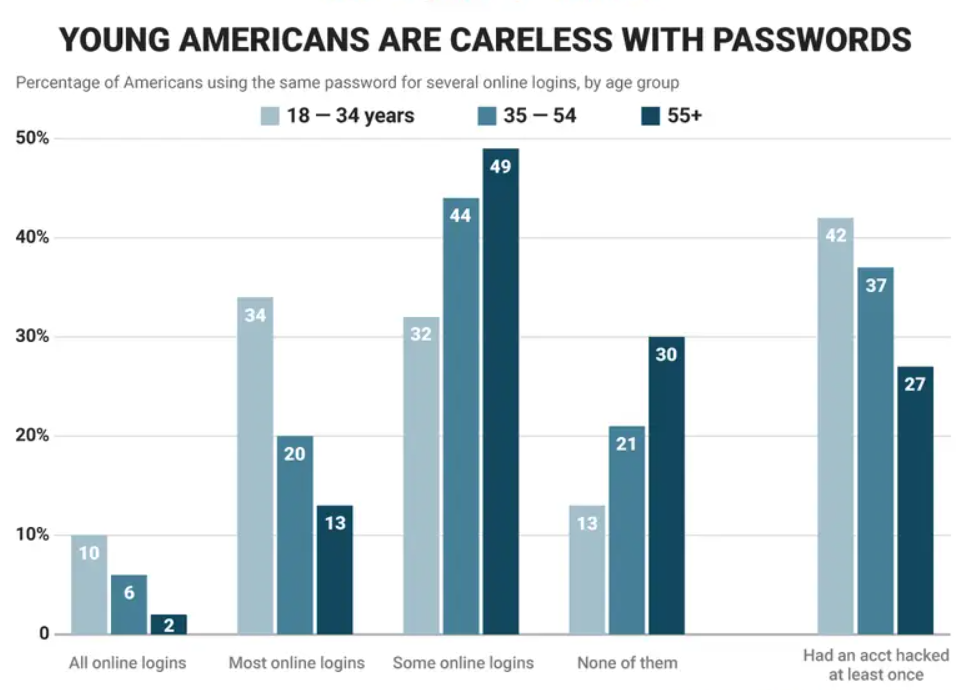
Hacking Email and Exploiting it
Now that we know why hackers are interested in your email address, let’s discuss how they can exploit it. Here are some common techniques that hackers use:
- Password guessing: If the hacker can guess your email password, they can access all of your emails and any accounts that are linked to your email address.
- Phishing: Hackers can use your email address to send phishing emails to you or to other people in your contact list.
- Malware: Hackers can use your email address to send malware, such as viruses or spyware, to your computer.
- Social engineering: Hackers can use your email address to trick you into providing sensitive information, such as passwords or credit card numbers.
How Hackers Sell Your Email?
Now that the hacker has your email address and has exploited it, they may want to sell it on the dark web. Your email address can be sold for various purposes, such as:
- Spamming: Your email address can be sold to spammers, who will send you unwanted emails.
- Phishing: Your email address can be sold to other hackers, who will use it to send phishing emails to you or to other people in your contact list.
- Identity theft: Your email address can be sold to identity thieves, who will use it to steal your personal information.
How Hackers Store Your Email?
Once the hacker has your email address, they will want to store it somewhere safe. Here are some common storage techniques that hackers use:
- Databases: Hackers may store your email address in a database, along with other personal information, such as your name and password.
- Cloud storage: Hackers may store your email address in a cloud storage service, such as Dropbox or Google Drive, to keep it safe from prying eyes.
- Encrypted files: Hackers may encrypt your email address and store it in a file, which can only be accessed with a password.
How Hackers Use Your Email for Coordinated Attacks?
Once the hacker has your email address and has stored it somewhere safe, they can use it for coordinated attacks. Here are some common techniques that hackers use:
- Spear-phishing: Hackers can use your email address to launch spear-phishing attacks, which are highly targeted phishing attacks that are designed to trick you into providing sensitive information.
- Password cracking: Hackers can use your email address to crack your password, which can give them access to your email account and any other accounts that are linked to your email address.
- Brute force attacks: Hackers can use your email address to launch brute force attacks, which are designed to guess your password by using common words and phrases.
Hacking Gmail, Outlook and Yahoo Accounts
Hacking into Gmail, Outlook, and Yahoo accounts is a serious threat to individuals and businesses. Each email client has its own set of security features, but hackers can exploit vulnerabilities to gain unauthorized access. Here are some specific techniques that hackers may use to hack into these email clients:
Gmail: Gmail has a robust security system that includes two-factor authentication and encryption. However, hackers can still gain access through phishing scams. Hackers may send an email that looks like it is from Google, asking the user to verify their login credentials. If the user enters their login details, the hacker can then access their account. Additionally, hackers can use keyloggers or malware to capture the user’s password.
Outlook: Outlook also has strong security features, such as two-factor authentication and encryption. However, hackers can exploit vulnerabilities in third-party add-ons and extensions. These add-ons can provide hackers with access to a user’s email account. Additionally, hackers can use phishing scams or malware to gain access to the account.
Yahoo: Yahoo has had several high-profile data breaches in the past, which has put users at risk. Hackers can gain access to Yahoo accounts through phishing scams, keyloggers, or malware. Additionally, Yahoo has a password recovery feature that can be exploited. Hackers can use personal information about the user to answer security questions and reset the password.
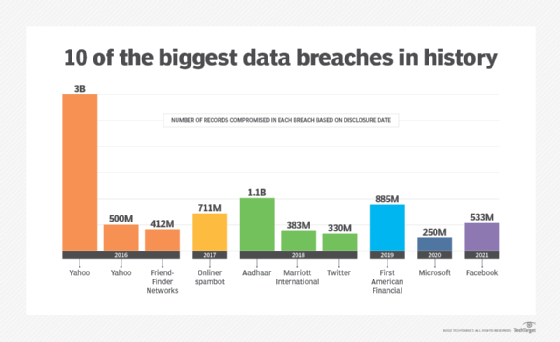
While each email client has its own set of security features, no system is foolproof. Hackers can exploit vulnerabilities and gain access to accounts. It is important for users to be aware of the risks and take steps to protect their accounts.
How Hackers Work with Third-Party Hacking Entities for Better Profit?
Finally, let’s discuss how hackers can work with third-party hacking entities for better profit. Here are some common ways that hackers collaborate with other hackers:
- Hacking forums: Hackers can collaborate with other hackers on hacking forums, where they can share information, tools, and techniques.
- Dark web marketplaces: Hackers can sell your email address on dark web marketplaces, where they can get a higher price for it than they would on the open market.
- Ransomware attacks: Hackers can use your email address to launch ransomware attacks, which can be used to extort money from you or from other people.
Best Practices to Protect Your Email from Hackers
Now that we’ve discussed how hackers can exploit your email address, let’s talk about some best practices that you can use to protect yourself:
- Use strong passwords: Use a strong password that contains a combination of letters, numbers, and symbols, and that is at least 12 characters long.
- Enable two-factor authentication: Enable two-factor authentication on your email account, which will require a code to be entered in addition to your password.
- Don’t click on suspicious links: Don’t click on links in emails that you don’t trust, especially if they are asking for sensitive information.
- Use antivirus software: Use antivirus software to protect your computer from malware, viruses, and other malicious software.
- Keep your software up to date: Keep your software up to date, including your operating system, web browser, and antivirus software.
- Be wary of public Wi-Fi: Be cautious when using public Wi-Fi, as it can be easily hacked and your data can be stolen.
In conclusion, email hacking is a powerful tool that hackers can use to gain access to your personal information. Hackers can obtain your email address through a variety of means, and can use it for phishing attacks, identity theft, spamming, and other nefarious purposes.
To protect yourself, use strong passwords, enable two-factor authentication, don’t click on suspicious links, use antivirus software, keep your software up to date, and be cautious when using public Wi-Fi. Stay safe out there!
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter. You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.








