

Google has issued a warning to Gmail users advising them to be cautious when checking their emails. The message, which appears as a red alert, cautions users to avoid clicking on links, downloading attachments, or replying with personal information, as similar messages have been used in the past to steal people’s personal information.
The warning also includes two buttons: one for reporting dangerous messages and another for indicating that the message looks safe.
Google encourages users to report potentially dangerous messages to help prevent others from falling victim to the same scam.
The red alert scam is a common phishing tactic used by cybercriminals to steal personal information. These scams are designed to look like legitimate emails from companies or individuals, but they often contain links or attachments that can download malware or steal login credentials.
In many cases, these emails appear to be urgent and may threaten dire consequences if the recipient does not act quickly. For example, an email might claim that there is a problem with the recipient’s bank account and urge them to click a link to “verify” their information.

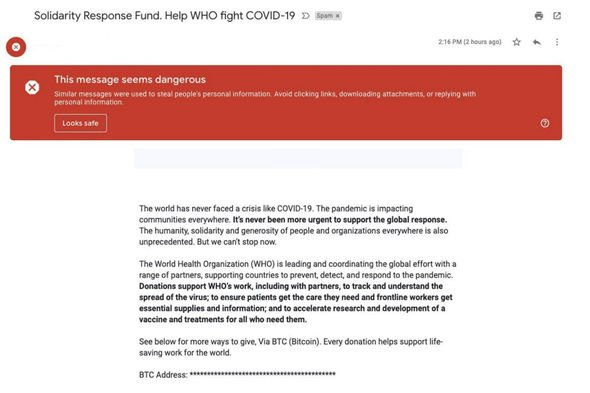
Unfortunately, many people fall for these scams, particularly if they are in a rush or not paying close attention.
According to data from Have I Been Pwned, a website that tracks data breaches and stolen information, there have been numerous reported incidents of successful phishing attacks in recent years.
To stay safe, it’s important to be vigilant when checking your email and to carefully examine any message that raises suspicions. Some red flags to watch out for include messages that come from unfamiliar or suspicious email addresses, messages that use threatening or urgent language, or messages that ask you to download attachments or click on links.
If you’re not sure whether an email is legitimate, it’s always better to err on the side of caution and report it to the appropriate authorities or delete it.
It’s also a good idea to keep your computer and software up to date with the latest security patches and to use strong, unique passwords for each of your online accounts.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…