Hackers send Teddy Bears and USB drives as gifts to deploy malware

F1N7 cybercriminal group are sending malicious USB drives and teddy bears through the United States Postal Service, deploying malware through booby-trapped USB drives. These USB devices can behave as a keyboard when connected to a computers, inject Powershell commands to execute a JavaScript, and deploy a malware called GRIFFON. The FBI had warned the businesses and front line actors to be aware of this threat in disguise.
The booby-trapped USB trick which security professionals and penetration testers have used are the fundamentals behind this attack structure. One such business had received a package from the USPS, and it had Best Buy Gift Card of $50 USD and a USB drive which is mentioned to have the list of products that can be purchased using that gift card. In recent times, USB drives are more than just a storage device, it can be used as a Human Interface Device (HID) which would convert them to keyboards, microphones or a mouse to deliver inputs automatically using a pre-programmed codes. This exactly has been used in this attack, please find the anatomy of this Teddy Bear USB drive attack below,
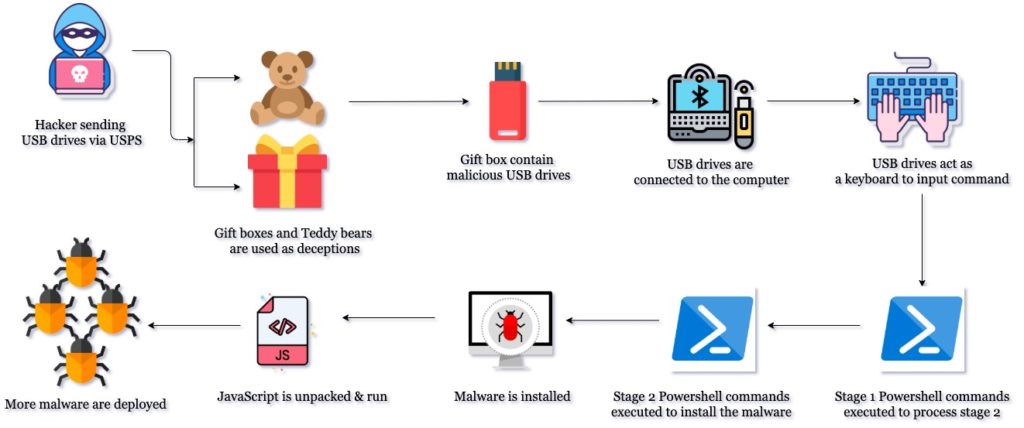
Security researchers from Trustwave studied this attack and found out that there is actually 3 unique Powershell commands that are being invoked and executed via these USB drives, leading to the installation of the malware in the computer that is connected to this USB drive. On investigating the USB drives further, the FBI had found the drives to be from Arduino Leonardo, using the micro controller ATMEGA24U and ATMEGA32U4, which is mostly costs below $14 USD.
Users can protect their computers in three different steps, keep an eye for malicious packages and teddy bears, the flag is red if you find a USB drive with or without, gift cards and never plug in the drives to the computers. While on the other hand, enterprises can employ USB security management applications to restrict devices that are unrecognized and keep their device control configurations updated. They can also updated the Powershell and turn ON the logging to identify the attack vectors.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.





