IKEA hit by a specially orchestrated phishing attack

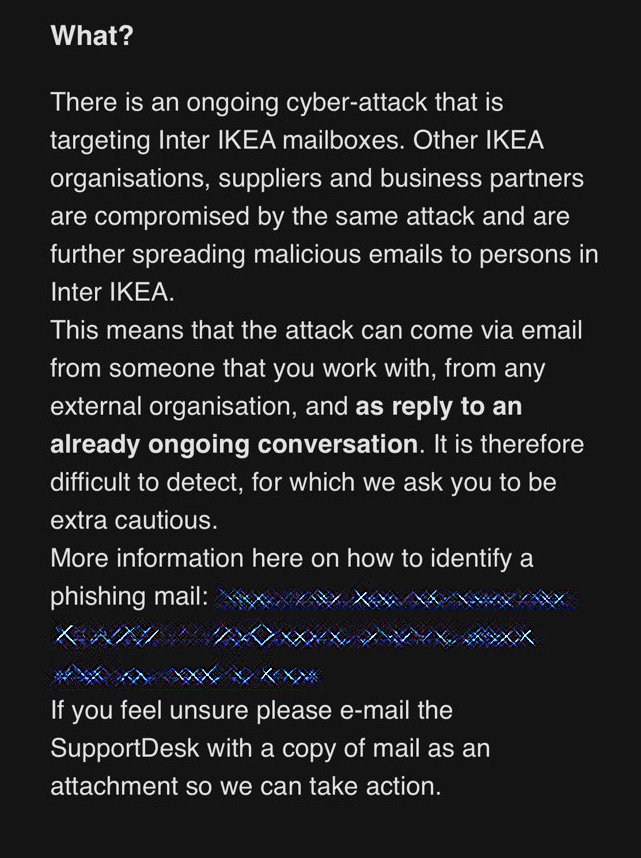
IKEA became a victim to a ongoing cyberattack on June 26th, and was battling the same as their employee email accounts were targeted for the internal phishing attacks.
The attack was identified to be reply-chain email attack when criminals steal legitimate email id of employees, and then respond to the employees with malicious attachment which will later install a malware in the recipient device.
Since the emails are sent from a legitimate account the employees are more likely to open it and thus the malicious documents can be triggered when clicked or downloaded.
Whats the effect of this IKEA Cyberattack?
IKEA has already warned its employees about the ongoing phishing attack and improved its security posture by employing robust email security. Since these phished mails are also being sent from other organizations like partners, IKEA found it to be a challenging act.
After observing the pattern of the attack, the IKEA IT team warned its employees about the phishing mail that comes with links and seven digits at the end of the link, also shared an example to alert the employees. They were also asked to report the sender email id to the IT team to take necessary precaution and block that account.
The reason behind such legitimate looking phishing campaigns is because threat actors have recently compromised Microsoft Exchange Servers with the help of ProxyShell and ProxyLogin vulnerabilities. As these actors gain access to the servers, they then use the internal options to execute this chain attacks against employees.
Phishing attack to spread Emotet and Qbot Trojan
The attached document in those emails had a excel file which when opened asked employees to click the enable content or enable editing button. If the button is clicked then a macro will be executed which will download a file called besta.ocx, bestb.ocx and bestc.ocx.
As per security researchers, phishing campaigns that had used these macros in the past have been used to spread Emotet or Qbot Trojan malware. IKEA believes this attack is just a beginning and threat actors can use this further to perform higher level cyberattack which could be more lethal to the enterprise and hence is working to improve their overall security posture.








