Lazarus Hackers Perform Social Engineering on Linkedin and Deploy Malware Payloads

The North Korean hacking group known as ‘Lazarus’ recently targeted employees of a Spanish aerospace company through a clever ruse involving fake job opportunities.
This article delves into what happened, why it matters, and how the attackers carried out their operations.
What did Lazarus Hackers do?
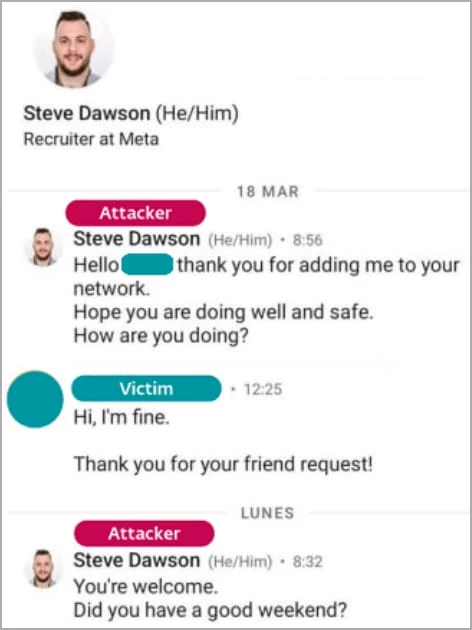
Lazarus hackers employed a scheme dubbed “Operation Dreamjob,” where they posed as recruiters, specifically someone named Steve Dawson from Meta (Facebook), on LinkedIn.
The attackers initiated a fraudulent recruitment process that eventually required victims to download a file.
Why is the cyber incident very sensitive?
As part of this scheme, victims were coerced into proving their proficiency in C++ programming by downloading quiz executables shared as ISO files. These executables unwittingly dropped an additional payload onto the victim’s machines, enabling the hackers to infiltrate the corporate network.
How did Lazarus Hackers orchestrate the attack?
The payload included the NickelLoader, a malware loader, which deployed two backdoors: a variant of BlindingCan with reduced functionality and a previously undocumented backdoor named ‘LightlessCan.’ LightlessCan, identified as a successor to BlindingCan, offers enhanced functionality and stealth by mimicking native Windows commands.
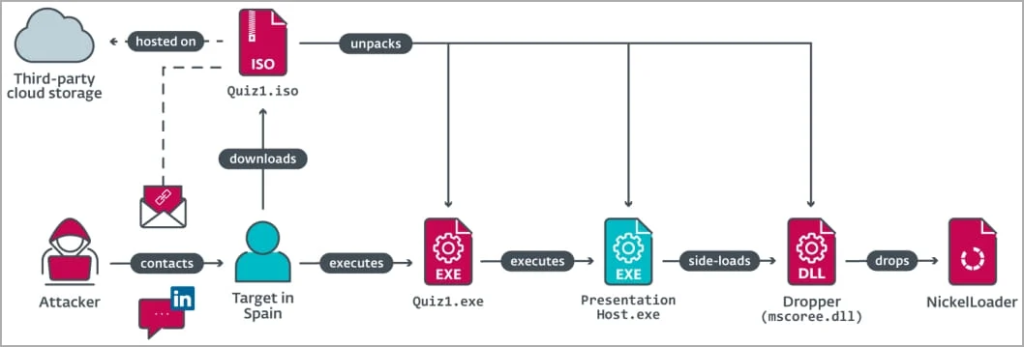
ESET, during their investigation, found that LightlessCan’s payload was encrypted and could only be decrypted in the target’s unique environment. This security measure indicates that Lazarus’ motives extend beyond financial gain, encompassing espionage objectives.
The Lazarus hacking group’s ‘Operation Dreamjob’ highlights the evolving tactics of cybercriminals. Their use of LinkedIn for social engineering and the introduction of LightlessCan as a sophisticated backdoor underscore the need for heightened vigilance among organizations facing threats from this North Korean threat group.
As a predecessor to this attack, the Korean National Police Agency (KNPA) has already issued a warning regarding a network breach at Seoul National University Hospital (SNUH). This breach, attributed to North Korean hackers, occurred in May 2023 and resulted in the illicit acquisition of sensitive medical data and personal information.








