Medusa Android Banking Trojan distributed via Flubot’s Attacks Network

According to new research ThreatFabric, two new Android banking Trojans named FluBot and Medusa are relying on the same delivery vehicle as part of simultaneous attack campaign.
The Dutch mobile security firm said, ‘the side-by-side infections that is facilitated through same smishing infrastructure, involved the overlapping usage of app names, package name, and similar icons’.
What is Medusa Android Banking Trojan?
Medusa Android Banking Trojan can manipulate accessibility permissions in Android to siphon funds from banking apps to an account controlled by the attacker. The Medusa Android Banking Trojan was first discovered by a Turkish financial organization in July 2020.

The researchers said that the Medusa sports other dangerous features like keylogging, accessibility event logging, and audio and video streaming — all these capabilities provide actors with almost full access to [a] victim’s device.
This malware-ridden apps is used in conjunction with FluBot masquerade as DHL and Flash Player apps to infect the devices. In addition, the Medusa Android Banking Trojan attack have expanded their focus beyond Turkey to include Canada and the U.S, with the operators maintaining multiple botnets for each of its campaigns.
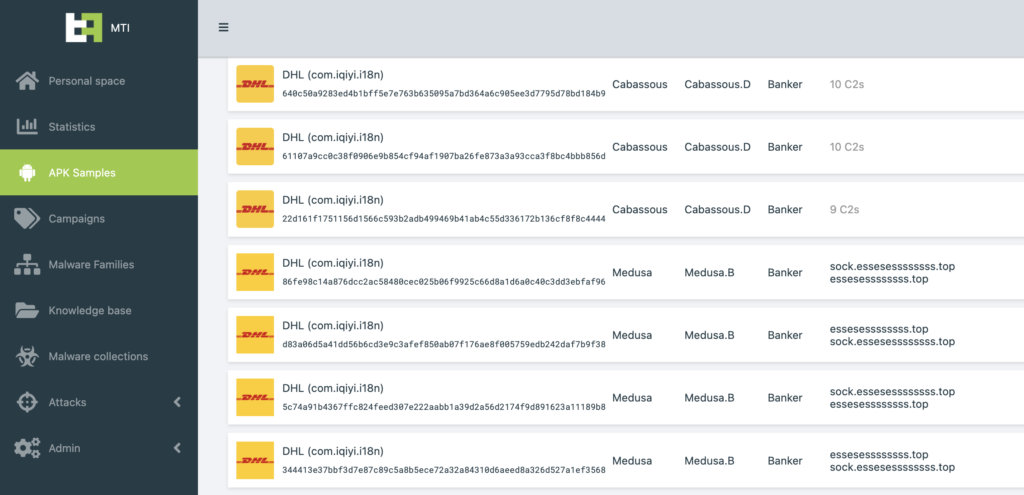
Details on Medusa Android Banking Trojan and FluBot attack network
The FluBot banking Trojan are a novel upgrade of its own, as it is able to intercept and abuse notifications from applications on a victim’s Android device by leveraging the direct reply action, alongside auto-replying to messages from apps like WhatsApp to spread phishing links in a worm-like fashion.
“With this functionality, this malware can provide [command-and-control server] supplied responses to notifications of targeted apps on the victim’s device,” the researchers said, adding the functionality “can be used by actors to sign fraudulent transactions on victim’s behalf.”
Android malware has already been seen to propagate by creating auto-replies to messages in WhatsApp. Last year, Check Point Research and ESET uncovered the rogue apps posing as Netflix and Huawei mobile that used the same technique to peform worm like attacks.
“More and more actors follow Cabassous’ success in distribution tactics, appropriating masquerading techniques, and using the same distribution service,” the researchers said. “At the same time, Cabassous keeps evolving, introducing new features and making another step towards being able to perform on-device fraud.”
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.





