

Microsoft has released its patches for the March Patch Tuesday which includes patches for an alarming count of 117 vulnerabilities, making it the biggest Patch Tuesday till date. Out of those 117 vulnerabilities in Microsoft Patch Tuesday March 2020, 26 were marked critical, 88 were mentioned as important, and 3 has been marked as moderate vulnerabilities. In Feb 2020, Microsoft patched 99 security vulnerabilities and this time has exceeded it. System administrators and end users are advised to update their systems with these security patches.

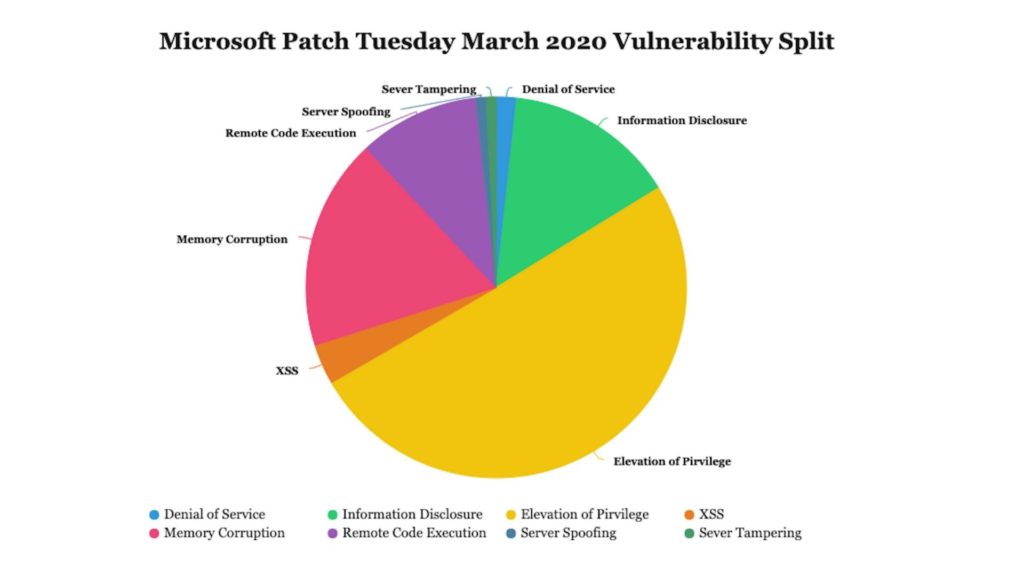
In Microsoft Patch Tuesday March 2020, security professionals and system administrators were expecting a patch for the SMBv3 vulnerability CVE-2020-0796 during the Patch Tuesday March 2020, but unfortunately that wasn’t rolled out. The severity of this vulnerability is that a remote code execution in the Server Message Block 3.0 could allow attackers to infect computers within a network similar to the EternalBlue vulnerability.
So while you have patched your systems for this month’s Patch Tuesday updates, also ensure you patch your systems for CVE-2020-0796 as soon as the Microsoft roll’s out the patch for the vulnerability. Another vulnerability CVE-2020-0684 is another remote code execution which exits in the .LNK file, attackers can modify this file and share it with the target, this crafted .LNK file will contain malicious macros which will be used to infect the targeted device. While CVE-2020-0852 is another remote code execution vulnerability in MS word, that could allow attackers to create malicious word documents, distribute it via mail and when opened the malicious behaviour of the file could infect the targeted systems.
There are four critical memory corruption vulnerabilities: CVE-2020-0801, CVE-2020-0807, CVE-2020-0809, CVE-2020-0869 that could take control of the victim’s machine to create new accounts, edit or delete data, and more. A simple malicious attachment or a web page could be the trigger for this vulnerability as the attackers could have embedded the malicious code in the attachment which would do the job of infecting the system.
More remote code execution vulnerabilities: CVE-2020-0824 and CVE-2020-0847 exists in VBScript engine and attackers can exploit again using a malicious web page or attachment. To execute this attack successfully, attackers would need a human interaction and for this we believe a social engineering methodology would be adopted.
The other critical vulnerabilities in Microsoft Patch Tuesday March 2020 that needs to be patched are,
Please take a look at the Microsoft Patch Tuesday March 2020 important and moderate security vulnerabilities and patch them to the earliest, also meanwhile do not forget the non-security updates. Though the latter may not appear to be urgent, they are required for efficiency and issue free working of the applications.
Enterprises are advised to deploy the security patches only after testing them in the test environment before deploying it to the production environment. Last Patch Tuesday had some cases where system administrators were forced to roll back their patches for a couple of reasons. So please wait for a week or two if you are concerned about productivity or deploy them immediately if security is your primary concern.
You can make use of Microsoft WSUS to deploy the Microsoft Patch Tuesday March 2020 patches. If in case you already own the SCCM, this should be easy for you, else employ a third party patching solutions for automating the download, testing, approval and deployment of patches.
Subscribe to ‘The Cybersecurity Times’, for daily alerts on cyber events. You can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…