

A hacker group called Moses Staff is incorporating an undocumented Remote Access Trojan (RAT) that disguises as a Windows Calculator App to go stealth.
The Moses Staff Hacker Group has been known for the series of cyber espionage attacks on Israel Organizations in 2021 and is also operating under political influence.
Cybereason, a cybersecurity company has been studying the activities of this Iran-based hacker group Moses Staff and has dubbed their recent RAT manipulation as StrifeWater.
This new RAT is used in the beginning of an attack to maintain stealth and remove itself after the goal is achieved. Tom Fakterman, Security Analyst at Cybereason said ‘The RAT possesses other capabilities, such as command execution and screen capturing, as well as the ability to download additional extensions’

Moses staff has been known since the end of last year when Check Point Researchers identified several attacks targeting Israel since Sept 2021.
Unlike other ransomware operators Moses Staff doesn’t aim for financial gains, instead focuses on disrupting organizations operations by encrypting the data and leaving it like that without ransom demands.
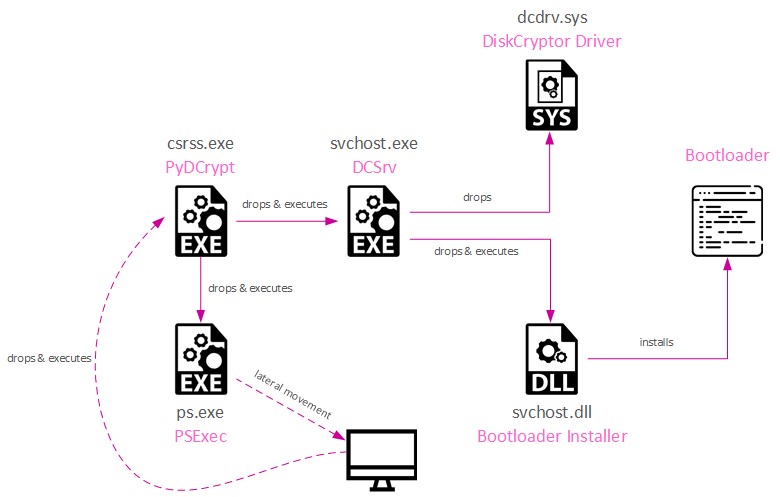
The intrusions were prominent as they depend on open-source library DiskCryptor to execute volume encryption, along with affecting the devices with bootloader that prevents the devices to start without the right encryption key.
As of Feb 02, 2022, the victims of Moses Staff are beyond Israel, starting with India, Germany, Chile, Italy, Turkey, the USA and U.A.E. The new StrifeWater RAT is deployed as calc.exe (windows calculator) and is deployed during initial stages of attack and is removed later post encryption of documents.
After the removal the calculator binary is replaced with a legitimate one, making it completely stealthy and facilitate the evasion phase of the attack once the ransomware payload function is successfully executed.
Highlights of StrifeWater RAT,
While ransomware operators like REvil, NightSky and others look for financial benefits, threat actors like Moses Staff and their StrifeWater RAT is where the organizations are concerned as their motive is just to disrupt the normal operations which is even more sinister than the former groups.
The discovery of new PyDyrcypt malware samples shows that the Iranian APT group Moses Staff is active and continues its nefarious acts on development of its attack arsenal.
Employing a Endpoint Detection and Response (XDR) system with the definition for Moses Staff StrifeWater RAT can help your network stay vigilant against this new threat.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…