
A dangerous botnet known as MyloBot has compromised thousands of systems across the globe. Most of the affected machines are located in India, the U.S., Indonesia, and Iran, according to a new report from BitSight.
The botnet, which has been active since 2017, is “currently seeing more than 50,000 unique infected systems every day,” with a high of 250,000 unique hosts in 2020.
MyloBot Botnet is a sophisticated botnet that emerged in 2017 and has compromised thousands of systems across the globe. The malware is capable of establishing a connection to a hard-coded C2 domain embedded within it and awaiting further instructions.
Its primary function is to download and execute any type of payload after infecting a host. MyloBot is also known for its anti-analysis techniques, making it challenging for security researchers to detect and analyze the malware. The botnet is actively evolving over time, and it continues to pose a significant threat to cybersecurity.
MyloBot and Mirai Botnet are two different types of botnets, and they differ in their architecture, methods of propagation, and purposes.
Mirai Botnet first appeared in 2016 and is known for infecting Internet of Things (IoT) devices, such as routers, cameras, and DVRs. The botnet uses default login credentials and known vulnerabilities to infect the devices, and it is often used for launching Distributed Denial of Service (DDoS) attacks. Mirai Botnet is designed to overload the target system with traffic, rendering it inaccessible.
On the other hand, MyloBot is a more sophisticated botnet that targets a broader range of devices, including desktops, laptops, and servers. MyloBot’s primary purpose is to establish a connection to a hard-coded C2 domain embedded within the malware and await further instructions. Unlike Mirai, MyloBot is not designed specifically for DDoS attacks, although it can download and execute any type of payload after infecting a host.
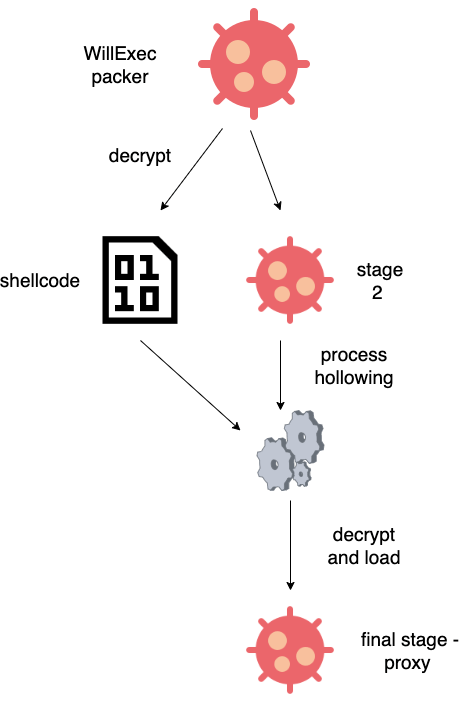
MyloBot also employs anti-analysis techniques, which makes it harder for security researchers to detect and analyze the malware. It sits idle for 14 days before attempting to contact the command-and-control (C2) server, sidestepping detection.
Both MyloBot and Mirai Botnet are dangerous botnets, they differ in their architecture, methods of propagation, and purposes. Mirai targets IoT devices and is often used for launching DDoS attacks, while MyloBot targets a broader range of devices and can download and execute any type of payload after infecting a host.
BitSight’s analysis of MyloBot’s infrastructure has uncovered connections to a residential proxy service called BHProxies. This suggests that the compromised machines are being used by the latter. The primary function of the botnet is to establish a connection to a hard-coded C2 domain embedded within the malware and await further instructions.
MyloBot was first documented by Deep Instinct in 2018. The malware employs a multi-stage sequence to unpack and launch the bot malware. It also sits idle for 14 days before attempting to contact the command-and-control (C2) server to avoid detection. Furthermore, MyloBot’s anti-analysis techniques make it challenging for security researchers to detect and analyze the malware.
MyloBot is a highly sophisticated and dangerous botnet that continues to evolve over time. Its ability to download and execute any type of payload after infecting a host makes it a significant threat to cybersecurity. BitSight’s findings highlight the need for organizations to implement robust security measures to protect against this and other types of malware.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…