New Bumblebee malware has complete stealth and can deploy ransomware

Bumblebee malware is back again this time with a new version that is featuring a infection chain that uses the PowerSploit framework for stealthy reflective injection of a DLL payload into memory.
What is Bumblebee malware?
Bumblebee malware involves phishing campaign that is orchestrated by Bazarloader and TrickBot operators, aka Conti Sydnicate. The malware was first discovered in April. The Bumblebee malware is an evolved loader with exceptional anti-detection and anti-analysis capabilities, it was expected to replace BazarLaodedr to deploy ransomware after the initial compromise.
As per a report by Cyble, the authors of Bumblebee malware are in plans for summer hiatus of spam operation with an updated workflow.
Modus Operandi of Bumblebee Malware
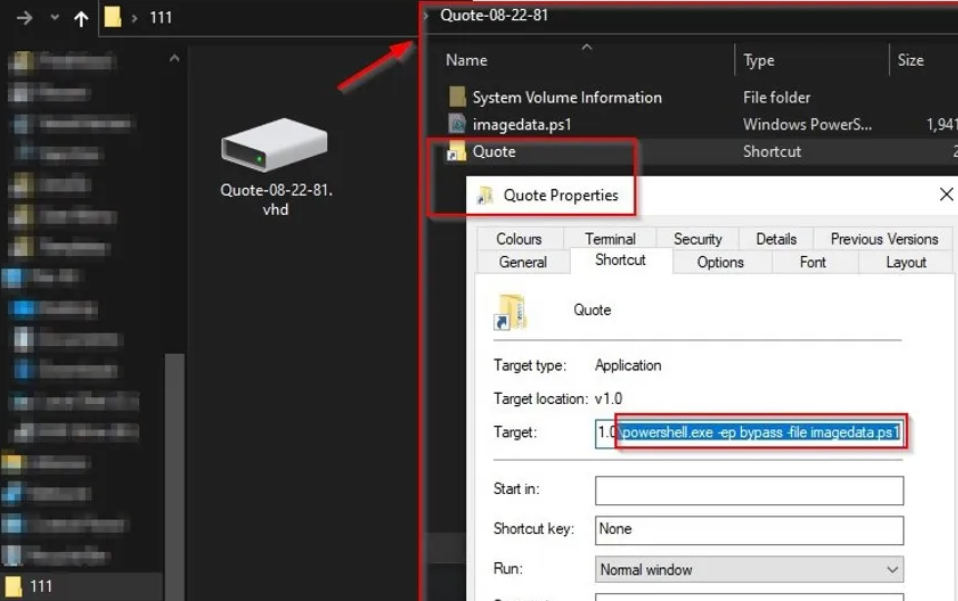
It begins with a phished e-mail that contained a password-protected zipped ISO files with an LNK and a DLL file. The recent attack had Bumblebee replaced its ISO with a VHD and the LNK file.
LNK executes ‘imagedata.ps1’ instead of the DLL using a PowerShell windows and keeps it invisible to the user by exploiting the ‘ShowWindow’ command.
The SP1 script is obfuscated using Base64 and string concatenation to evade antivirus detection while loading the next stage of the PowerShell loader.
The next stage has the same obfuscation initially and then the PowerSploit module to execute the 64-Bit malware into the memory of PowerShell process usign the reflective injection.
“PowerSploit is an open-source post-exploitation framework in which the malware uses a method, Invoke-ReflectivePEInjection, for reflectively loading the DLL into the PowerShell Process.
This method validates the embedded file and performs multiple checks to ensure that the file is loaded properly on the executing system.” as per the Cyble report.
This malware can also load the flow from the memory and never touches the disk, which is why it escapes detection by endpoint security software. With better stealth, Bumblebee malware becomes more dangerous and has the potential of deploying ransomware and other malicious activities on the infected devices.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter. You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.








