New phishing campaign drops two payloads in ‘Dali Masks’ threatening device security

One security researcher has identified a new phishing campaign that is distributing a LokiBot info-stealing malware and another payload called the Jigsaw Ransomware.
Hackers are now deploying more than one malware to ensure their attack is organized streamlined with better success rates. Hackers use this malware combo, to steal the usernames and passwords of different applications first, then they deploy the ransomware demanding ransom for the encryption.
This phishing campaign had attachments that had impersonated invoices, bank transfers, business inquiries, orders and more. Excel attachments such as Swift.xlsx, order.xlsx, Inquiry.xlsx and Invoice for payment.xlsx is used to lure the victims to download these attachments. A legitimate looking spreadsheets is the mere advantage for hackers, as most recipients will believe that those attachments are from the actual source itself.
Jame, a security researcher has identified this campaign, and mentioned that the attachment are weaponized with LCG kit, exploiting an old remote code execution vulnerability in Microsoft Office tracked as CVE-2017-11882 in Equation Editor.
How does this new phishing campaign work?
If the attachment is downloaded, the instructions in the file will download the malware from a remote site and starts executing its intended process. James had disclosed the cjjjjjjjjjjjjjjjjjjj.exe file, is the LokiBot and has the capabilities to steal credentials from mail, browsers, FTP, and other terminal applications. After stealing the details, it transfers the information through command and control server to the creators of the campaign.
Meanwhile, LokiBot also initiates the second attack vector by downloading and installing the Jigsaw Ransomware variant that has employed Salvadore Dali mask that was used in the popular Spanish series ‘Money Heist’.
Like any other ransomware, Jigsaw also encrypts the victims files and folders, and starts deleting the encrypted files until the ransom is paid. However, this ransomware can be decrypted easily compared to others.
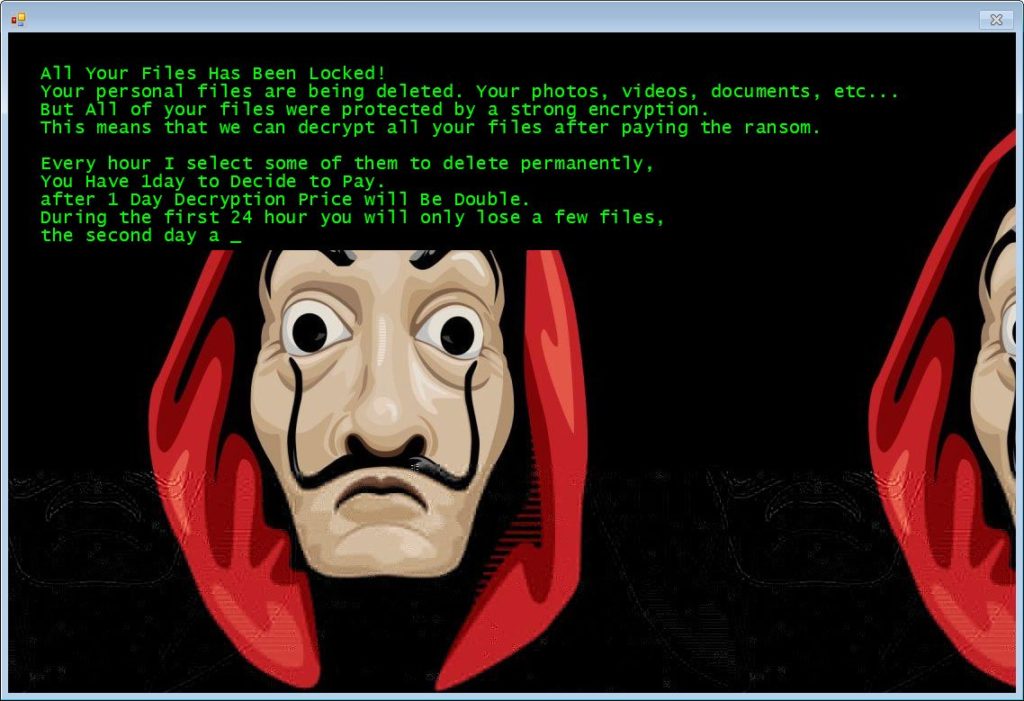
How to get rid of Jigsaw ransomware?
If you are infected by this ransomware, ensure you terminate drpbx.exe process from your Task Manager, and this will help you secure your files from deletion.
Additionally, updating your Microsoft Office to the latest versions, especially Excel could ensure you are protected against these twin payload deployments on your devices.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.








