

Information stealing malware under the Stealer-as-a-Service model is being distributed by 34 Russian Cybercrime Group. The infostealer has now successfully stolen 50 million passwords in 2022.
As per a report published by Group IB, “The underground market value of stolen logs and compromised card details is estimated around $5.8 million”.
The infostealer malware has the stolen passwords, and have harvested 113, 204 crypto wallets, 2.11 billion cookie files and 103, 150 payment cards as well.

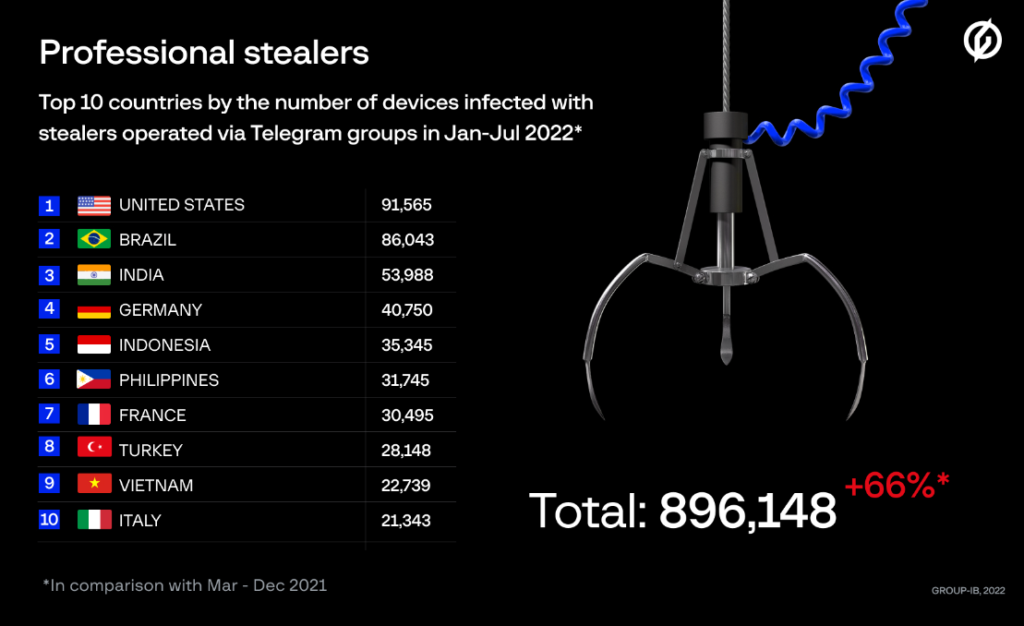
Most of the victims of this malware are from the USA, Brazil, Germany, Indonesia, India, Philippines, Vietnam, Italy, France and Turkey. In overall, around 111 countries and their 890,000 devices were infected by the infostealer malware.
As per the Group IB researchers the Russian Cybercrime Groups have previously participated in the Classiscam Operation already. The hackers have been active on the Telegram with 200+ members in their channel.
The members orchestrate the deployment of infostealer malware using bait website that impersonate popular brands and manipulates users into clicking links.
These links were found in Youtube Video Reviews on Games, Lotteries and other social media platforms.
“Administrators usually give workers both RedLine and Racoon in exchange for a share of the stolen data or money,” the company said. “mentioned Group IB researchers, stating few use one infostealer malware while others use maximum of three infostealers.
After successful deployment and compromise of the targeted individuals, the data of the users is then sold in the dark web for monetary benefits.
Telegram though is a privacy first chat application, lately it has been found to be brewing grounds for malicious and nefarious entities.
The threat actors are releasing product updates, roadmaps and exfiltrate data samples to market and generate demand for their illegal activities.
As per another report from SEKOIA, there has been seven new traffers teams that has included the infostealer malware known as Aurora to thei threat toolset.
The findings also follow a new report from SEKOIA, which disclosed that seven different traffers teams have added an up-and-coming information stealer known as Aurora to their toolset.
“The popularity of schemes involving stealers can be explained by the low entry barrier,” Group-IB explained. “Beginners do not need to have advanced technical knowledge as the process is fully automated and the worker’s only task is to create a file with a stealer in the Telegram bot and drive traffic to it.” said the researchers.
The internet has been flooded with several new malware, including RapperBot, SocGholish, Bumblebee and more.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…