Russian Hackers APT29 Exploits WinRAR Vulnerability

Russian hacker group APT29, also known as UNC3524, NobleBaron, Dark Halo, NOBELIUM, Cozy Bear, CozyDuke, and SolarStorm, has recently been identified leveraging the CVE-2023-38831 vulnerability in WinRAR for cyberattacks. This comes after similar activities by Sandworm and APT28 (Fancy Bear).
The CVE-2023-38831 security flaw affects WinRAR versions before 6.23, enabling threat actors to create .RAR and .ZIP archives capable of executing background code for malicious purposes. The vulnerability has been exploited as a zero-day since April, primarily targeting cryptocurrency and stock trading forums.
It is to be noted that another advanced persistent threat (APT) group called GoldenJackal also has been engaging in espionage against government and diplomatic entities in Asia since 2019 and exhibited notable activity in Afghanistan, Azerbaijan, Iran, Iraq, Pakistan, and Turkey, as reported by cybersecurity firm Kaspersky.
Russian Hackers APT29’s Modus Operandi and Targeting
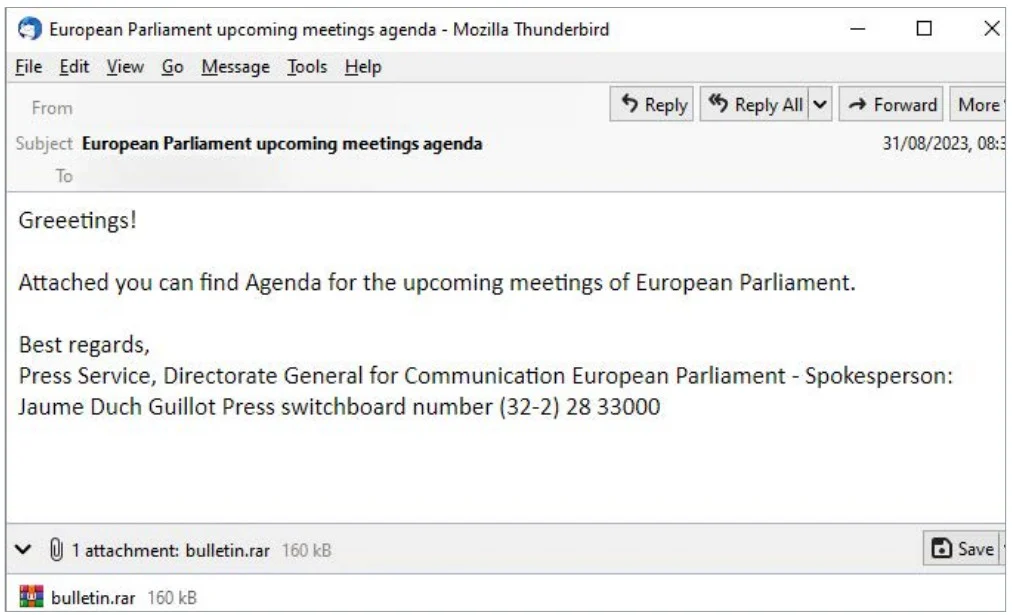
APT29 has been employing a BMW car sale lure to target embassy entities, using a malicious ZIP archive that executes a background script to display a PDF lure. The PDF then triggers the download of PowerShell code, leading to the execution of a payload.
The malicious archive, named “DIPLOMATIC-CAR-FOR-SALE-BMW.pdf,” has been used by APT29 to target multiple European countries, including Azerbaijan, Greece, Romania, and Italy. This phishing lure was previously employed in a campaign in May against diplomats in Ukraine.
Innovative Tactics: Ngrok for Communication
In a novel approach, APT29 has incorporated Ngrok, specifically its free static domains, for communication with the command and control (C2) server. This tactic allows the hackers to establish discrete rendezvous points, avoiding detection and enabling communication with compromised systems.
The Ukrainian National Security and Defense Council notes that APT29’s campaign stands out for its combination of old and new techniques. The WinRAR vulnerability is used to deliver payloads, while Ngrok services are employed to conceal communication with the C2 server.
Widespread Exploitation of WinRAR Vulnerability
Security researchers have observed the exploitation of the CVE-2023-38831 vulnerability by advanced threat actors, including APT28, who targeted political entities in the EU and Ukraine in a spearphishing campaign. Google’s October report highlighted its use by Russian and Chinese state hackers for stealing credentials and sensitive data.
The Ukrainian NDSC report provides a set of indicators of compromise (IoCs), including filenames, corresponding hashes for PowerShell scripts, an email file, domains, and email addresses associated with APT29’s cyberattacks.








