Top 6 Best Vulnerability Management Software for 2024

Network security is a critical aspect of any enterprise and firms need solid security protocols to handle their network vulnerabilities. Any data breaches could cost millions for businesses affecting their operations, reputations, production and customers.
With a vulnerability management tool, companies can ensure their network security is always updated and can ensure better protection of assets overall.
In this article, we’ll see how vulnerability management software can facilitate enterprise network security and ensure their data is protected from external threats.
What is Vulnerability Management Software?
The process of scanning an entire network to identify vulnerabilities and provide remediation to fix the situation and the vulnerability, say it be temporary or permanent, and ensure such threats are detected in advance and fixed promptly is called Vulnerability Management.
The tool that facilitates the whole process by allocating degrees or levels of critical vulnerabilities is called the Vulnerability Management Software. This is a proactive cybersecurity tool and is different from antivirus and firewall which are reactive tools.
Why will Vulnerability Management Software make a difference?
Attackers often exploit the existing vulnerabilities in any organization. They try to exploit the zero-day vulnerabilities, port vulnerabilities, device vulnerabilities, or firmware vulnerabilities to breach network security and exploit the data associated with those devices and their connected applications.
When companies employ a vulnerability scanner and vulnerability management software, they are ready for external attacks with robust security in place. Attackers won’t find the loopholes and their attempts will only fail.
How to choose Vulnerability Management Software?
While evaluating the options in the market we must know the key capabilities to look for in a vulnerability management software. These key features are fundamental for an efficient vulnerability management tool that will give businesses and IT professionals an upper hand against cyber criminals,
- Vulnerability Scanner
- Detection and Description of vulnerabilities
- Patch management
- Custom scripts for zero-days
- Alerting and Reporting
Vulnerability Scanner
The vulnerability management software must come with an effective vulnerability scanning agent that should cover all the network devices and endpoints holistically. The range of coverage is important as it determines the vulnerability spread across the enterprise network.
Detection and Description of vulnerabilities
Companies need to detect and identify vulnerabilities at the right time to avoid their exploitation affecting their network and the data associated with it. A vulnerability management software should be able to identify and also give a brief description of the vulnerability to enable IT security professionals and the SOC team to understand and act on it accordingly.
Patch management
Vulnerability management should come along with patch management as patching is the remediation stage after detection.
Custom Scripts for Zero-Days
Not all vulnerabilities come with vendor patches as soon as they are reported. When there is no patch available, the SOC team must be able to do a workaround for the same and deploy a custom script to mitigate the situation temporarily until a patch is officially released.
Alerting and Reporting
The vulnerability management tool should have user-friendly alerting of vulnerabilities. The alerts should give the details of the CVE and their description, if patches are available then should include that as well. The reporting should be automated and should support the breakdown of the vulnerability management process.
Top 6 Vulnerability Management Software – Best Vulnerability Management Tool for 2024
Vulnerability management tools should be an integral part of any company, and to do that here are the best five vulnerability management software that you can evaluate and choose from.
Tenable Vulnerability Management Software – Vulnerability Management Tool
Tenable provides visibility into all the devices and assets in the network, including vulnerabilities across the entire attack surface. This allows companies to assess everything, since malicious actors are already scanning your corporate network, it is good to do the same with Tenable as well.
The Tenable vulnerability management tool employs threat intelligence to detect and predict vulnerabilities that are critical to the network. Furthermore, the tools also showcase the description of the vulnerability with key metrics and insights for further action.
Price: $2275/year for 65 devices. 41497
Heimdal Security – Vulnerability Management Tool
Heimdal Security comes with automated patch management that will deploy and patch any Windows, Linux and third-party software across networks, branches and geos. Gives complete visibility into the granular control over entire software inventory. Update applications located anywhere in the world from one central location.
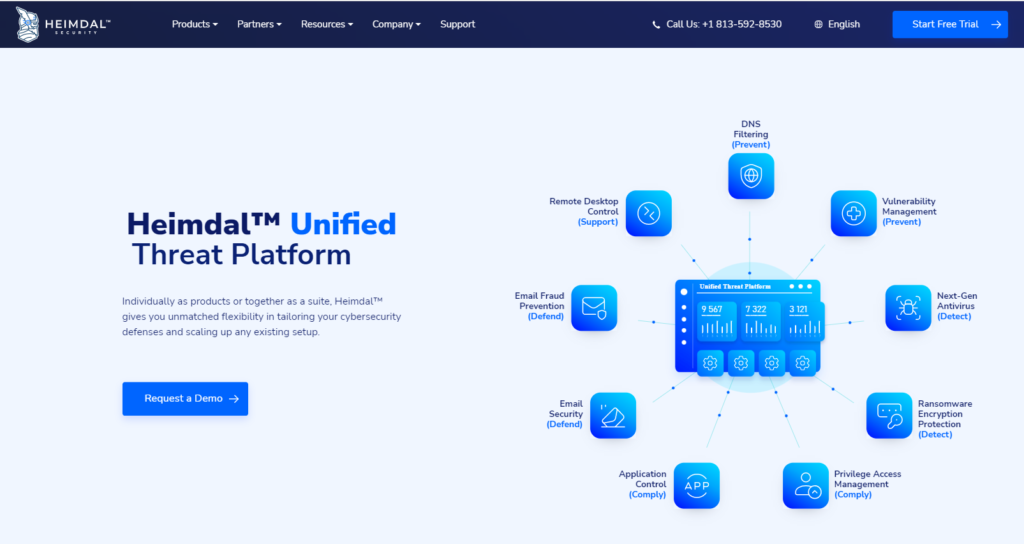
Offers unified threat intelligence that comes with DNS filtering, next-gen antivirus, ransomware encryption protection, remote desktop control, email security, email fraud prevention, and privilege access management.
Price: 16/year
ManageEngine Vulnerability Manager Plus:
Enhance your enterprise’s security with Vulnerability Manager Plus, a multi-OS solution offering end-to-end vulnerability management and compliance with built-in remediation. Ensure comprehensive coverage, continual visibility, and rigorous assessment from a single console.
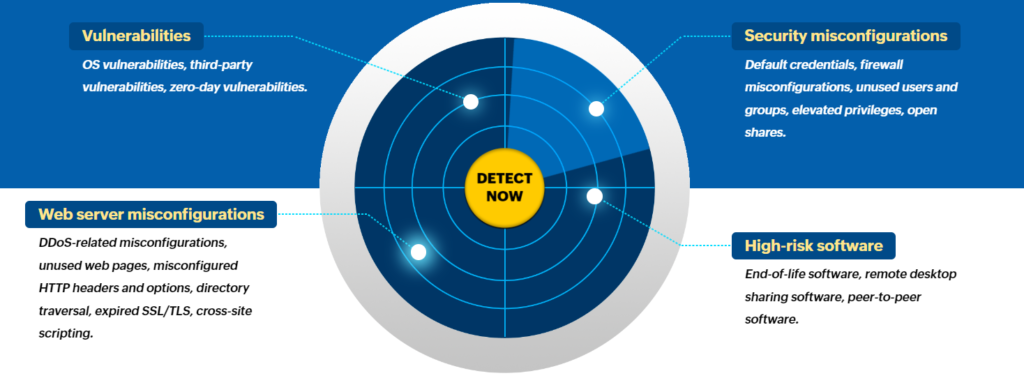
ManageEngine Vulnerability Manager Plus ensures robust security with features like comprehensive Vulnerability Assessment, effortless Compliance meeting 75+ CIS benchmarks, streamlined Patch Management for Windows, Mac, Linux, and 500+ third-party apps, enhanced Security Configuration Management, effective Web Server Hardening, swift High-Risk Software Audit, and prompt Zero-day Vulnerability Mitigation. Strengthen your security effortlessly.
Pricing: Starts at $1195 for 100 workstations annually.
Netsparker vulnerability management software – Invicti vulnerability management tool
Invicti Netsparker vulnerability software is an automated vulnerability management tool that scans web applications and services to detect vulnerabilities in their security. The scanning includes all applications, regardless of operating system.
The tool combines DAST and IAST for scanning to detect vulnerabilities. It is behaviour-based and signature-based and gives you accurate results on time. It is a ‘Proof Based Scanning’ feature that can automatically detect vulnerabilities to identify if they are false positives or real ones.
Price: $666/month.
Acunetix vulnerability management tool
Acunetix vulnerability management software can be deployed to scan and secure all types of websites and web applications. With Advanced Macro Recording feature that offers sophisticated multi-level forms of security. It is known to have identified 7000 vulnerabilities including databases, weak passwords, XSS and more.
The tool also reduces false positives as it double-checks vulnerabilities before reporting it to the subject of concern. It facilitates automated and scheduled scans ahead of time as per business requirements.
Price: $4495 per website
SecPod vulnerability management software
SecPod SanerNow Cyber hygiene is an automated and advanced vulnerability management tool that brings a new revolution to traditional patching. The integrated vulnerability assessment and patch management make the entire vulnerability management hassle-free. Detection of CVE vulnerabilities with instant mitigation and remedies makes SecPod unique and the best option for SMBs.
Supports major OS and devices with support for routers and switches. The unified console for vulnerability assessment and remediation makes the SecPod vulnerability management tool user-friendly.
Price: $50/year per device.
Give a try on all these vulnerability management tools, evaluate them for your network and see which suits your ecosystem and demands better.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter. You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.








