Top 5 Phishing Tools for 2024 – Best Phishing Simulation software

Verizon’s Data Breach Investigation Report claims phishing as the top-most threat of data breaches. Around 22% of the global cyber threats involve phishing. Likewise, the ‘Symantec’ statistics found mining, agriculture, forestry, public administration, construction, and wholesale trade are sectors with the highest phishing prevalence rate.
Indeed, there is no domain without phishing. This still and will remain a critical threat to individuals, businesses, organizations, and their financial cum personal accounts. Ultimately, brands can lose their reputation among the elite corporate communities. Overall, this social engineering strategy, along with the phishing simulation tools, is quite interesting to read. Check them from down below.
What is a Phishing tool?
You must have come across articles like these – where an official-looking or site email asks for a credit card or PAN number for verification. Nevertheless, that is a malicious prompt from some phishing tools. Victims unknowingly disseminate their confidential information and ultimately get caught in grave financial and personal troubles.
According to the Federal Trade Commission (FTC), phishing tools attack profiles by either of these means;
- An email might require a signature from you to acknowledge a fake invoice.
- An illegitimate company may offer you exclusive coupon codes and bonus offers.
- An unused, age-old account may notify you to update your personal information.
- An illicit site can claim it noticed suspicious activity and requires your re-login.
So, your awareness to detect phishing tools and their deceitful messages is paramount to digital safety!
Types of Phishing Attack
“Fishing” passwords happen in 15+ ways with various phishing simulation software available. Yet, these are the five phishing attacks that are oftentimes witnessed these days;
- Spear Phishing – This electronic communications scam is a threat to get private data from the victim; not just by acting legitimately but also the criminal tries to install malware on a targeted user’s computer.
- HTTPS Phishing – With the facility of Hypertext transfer protocol secure (HTTPS), scammers add a short-tail HTTPS code to their website and make the victims perform certain actions on the page.
- Deceptive Phishing – An untrustworthy email gets sent bulk to multiple sources. The purpose of such a misleading technique is to put a “Call To Action” (CTA) and get the recipient’s details, like bank account details.
- Pharming – A victim’s DNS server gets negotiated for redirecting them to a simulated website that steals their private information, even without making them click on a button.
- Whaling – Masquerading as a legal source, whaling is a phishing attack where only high-level senior executives are targeted to initiate steps, like wire transfer of funds.
The end intent of phishing is to hack and steal passcodes and specifications by faking as legitimate sources. Only the way of pretending and mode of communication varies accordingly. And hence your knowledge of using phishing simulation tools is a must!
Why is Phishing Simulation software important?
Recognizing, dodging, and reporting potential data threats is critical to both the common man and a business firm. Owing to that, we can stay protected to a possible extent by using phishing simulation software.
As the name states, create a ‘simulated’ environment and verify where and how our information is phish-able, probably. Even exclusive security training programs are conducted for employees to make them aware of these phishing tools.
Benefits of Phishing Tools
As a part of security awareness, we can build defensive human resources by understanding the depths of any phishing simulation software. Regardless of how big a corporation is, there would be minute security gaps. And software modules like these will help us detect and bridge those gaps.
Also, the key to using such phishing tools is to seriously reduce the overall cost spent when at times of a real cyberattack.
Top 5 Best Phishing Tools for 2024
So, ready to keep your personal information safe? Then, get to know about the features of the top 5 phishing simulation tools listed below;
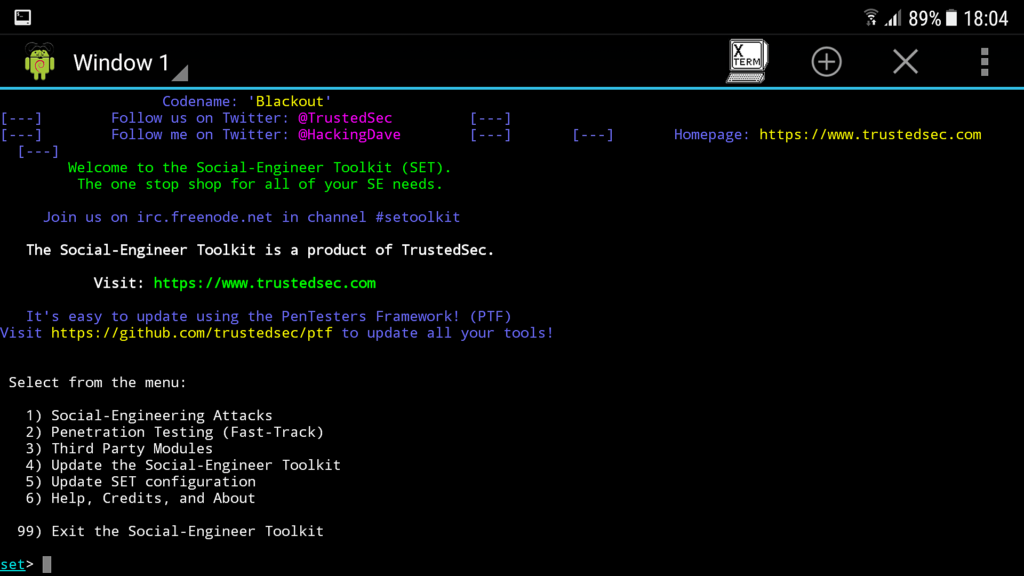
SEToolkit
If speed is your concern, then SEToolkit is your thing. From a mastermind ‘Dave Kennedy’ from ‘TrustedSec’, the Social-Engineer Toolkit is an open-source penetration testing Python framework. From fake phone numbers to dummy SMS messages, personalize anything important and attack instantly, free of cost.
Besides phishing, you can use SEToolkit even for Infection Media Generator, QRCode Attacks, and Arduino-Based Attack.
Give a try on these phishing tools and experience this phishing simulation software.
Highlights
- Multiple tweaks from the configuration menu.
- Custom attack vectors.
- Integration support with third parties.
- Multi-platform: Runs on Linux, Unix, and Windows.
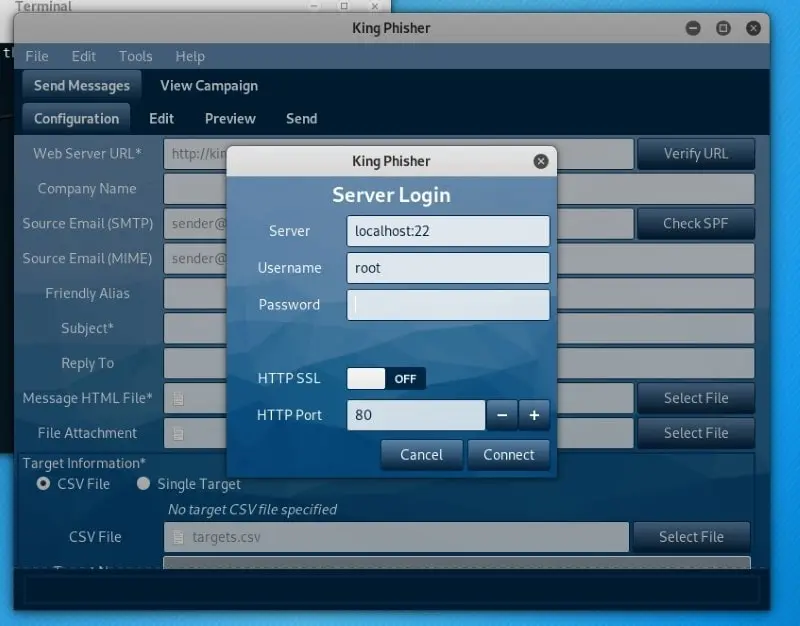
King-Phisher
Unlike the other complicated phishing tools known, King-Phisher has a user-friendly appearance. You can get 100% control over both the server content and emails with its extremely flexible architecture. If you operate a firm, then you need to get explicit permission before obtaining the database.
However, with a legal permit, you can make wonders with King-Phisher, owing to its alerts, options, and web page cloning capabilities.
Highlights
- Run multiple phishing campaigns simultaneously.
- Geolocation of visitors.
- Credential harvesting from landing pages
- Integrated Sender Policy Framework (SPF) checks
Give a try on these phishing tools and experience this phishing simulation software.
Evilginx2
With the aid of session cookies, the Evilginx2 phishing tools utilize the man-in-the-middle attack framework. It acts as a relay between the phished user and the actual website. You can even bypass the 2-factor authentication (2FA) protection. Since the entire program is pre-written in GO (as a standalone app), your setup is going to be simple. As of date, there are no vulnerabilities reported with its dependent libraries.
Highlights
- Customizable hostnames for each phishing lure.
- Generated URLs are exportable to file (text, CSV, JSON).
- IP black-list with automated address black-listing option.
- SOCKS5 and HTTP(S) proxy support routing connections.
Give a try on these phishing tools and experience this phishing simulation software.
HiddenEye
HiddenEye is a contemporary tool, well-suited for regular phishing and keyloggers (keystroke logging). The functional components and its brute force attack techniques are so good. 30+ famously global social media channels such as Instagram, Yahoo, Facebook, Snapchat, etc., can be easily phished. You need to have the Termux or UserLand application if you are an Android user.
Highlights
- Multiple Tunneling Services.
- Serveo URL type selection (between Custom and Random URLs).
- Live attacks with IP, geolocation, ISP, country, address, etc., are possible.
- A highly efficient tool for Enterprise level Penetration Test.
Give a try on these phishing tools and experience this phishing simulation software.
Infosec IQ
With its 1,000+ realistic phishing templates, Infosec IQ is an all-purpose name for both data breach simulation as well as security awareness training. Typosquatting, domain-specific spoofing, and similar tactics work here.
Generate your company’s initial phish rate for free, but at later use, you need to pay. Once done, you can even replicate in-the-wild, authentic attacks using real brand logos.
Highlights
- Around 300 international phishing templates are available with translated versions.
- USB, malware, business email compromise (BEC), malicious attachments, and more.
- Team quarantine features are available for actual incidents.
- Training modules can be pre-scheduled even for one full year.
Give a try on these phishing tools and experience this phishing simulation software.
Honorable Phishing Simulation Tools for 2024 – Best Phishing Tools
Three other phishing modules are getting quite popular with the penetration testers, blue and purple teams of this gen, and here they are;
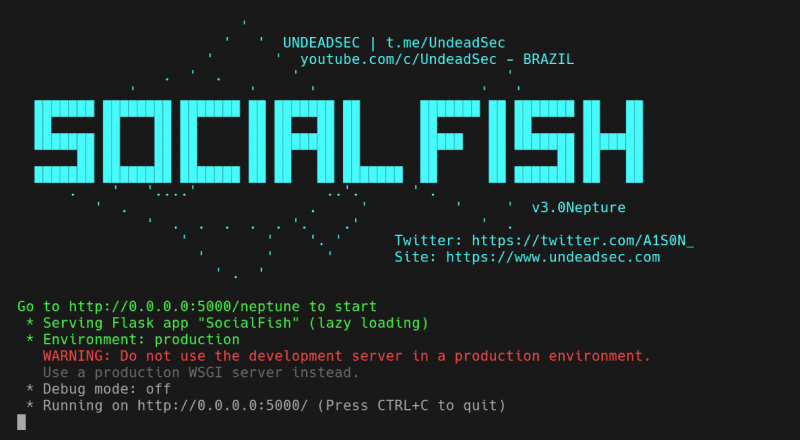
SocialFish
Known for its customizable links, SocialFish is one of the classic phishing simulation tools for convincing results with social media phishing. Its present version 3, plus the BSD-3-Clause License, make it ever-ready to harvest multiple LANs.
Python 3.6 or Greater and Pip3 are prerequisites to its installation. Above all, the biggest perk is that you can clone social media sites and form a password-harvesting attack link with just a few clicks.
Highlights
- Straightforward, web-based user interface.
- No need to create templates all by yourself.
- Kismet makes accessibility easier.
- A beginner-friendly toolkit.
Give a try on these phishing tools and experience this phishing simulation software.
Phishing Frenzy
Email phishing campaigns are unbeatable with Phishing Frenzy. Thanks to Brandon “zeknox” McCann in 2013 for creating this open-source Ruby on Rails app. As a data harvester, you will initially need the Bing API key for proper function.
Yet, once you avail of it, your first 5000 transactions are completely free of charge. Phishing Frenzy now also has an Email Harvester that helps you enumerate specific mails throughout the web.
Highlights
- Best campaign management tool.
- Template reuse.
- Statistical generation.
- Having a domain name is not mandatory.
Give a try on these phishing tools and experience this phishing simulation software.
Gophish
Powered by a REST API, Gophish has a super cool user interface. The data is extractable even for scheduled events and timelines that include tracking email opens, submitted credentials, link clicks, and more. And the red team exercises work best for users and groups, sending profiles and landing pages.
However, besides these, Gophish can bypass filters and reach inboxes if you pick different ship profiles for various users.
Highlights
- Pixel-perfect phishing templates.
- Accustomed to business clients and partners.
- Full HTML editor.
- Cross-platform support – Windows, Mac OSX, and Linux.
Give a try on these phishing tools and experience this phishing simulation software.
Trending Phishing Tools for 2024 – Best Phishing Simulation Software
Acceptable for their features, but yet-to-be widespread, here comes the final set of phishing simulation software modules that we hope could be useful for your security research;
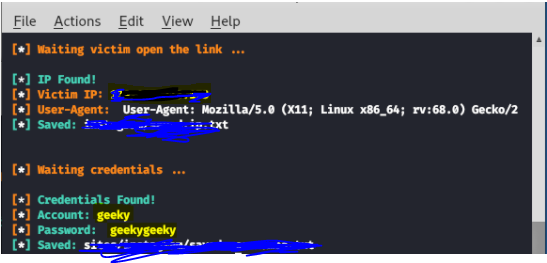
BlackEye
Since its foundation, Blackeye has worked across 38 global platforms, including Snapchat, Google, Instagram, Yahoo, PayPal, Spotify, Protonmail, GitHub, Protonmail, Twitch, Linkedin, etc. Hackers and credential harvesters have mostly preferred to use this tool through Kali Linux and Android via Termu. With ngrok introspectable tunnels, you can precisely execute a phishing assault, both outside and inside LAN.
Highlights
- 32 + 1 customizable templates.
- Stay connected with your target’s machine by port forward.
- Inbuilt arm support.
- Mobile version supported.
Give a try on these phishing tools and experience this phishing simulation software.
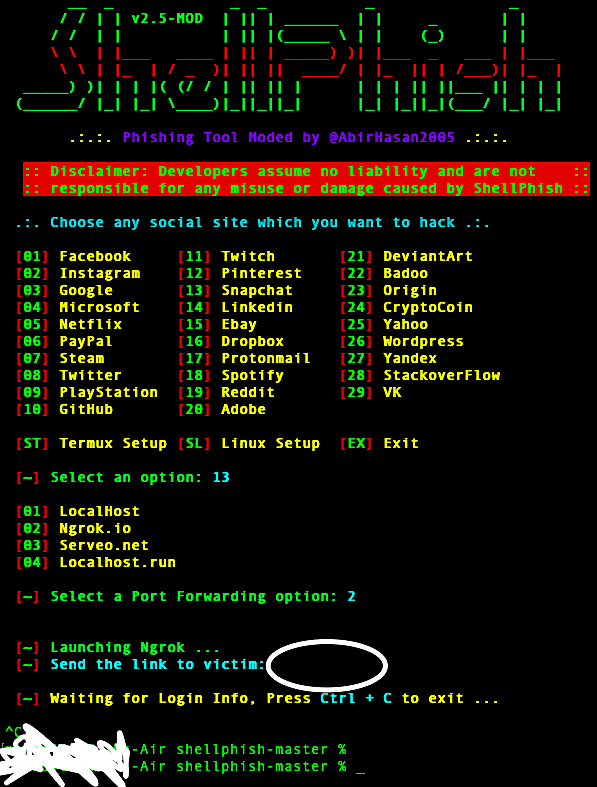
Shellphish
From Spotify and Dropbox to Reddit and DeviantArt, here’s another phishing simulation software, written by ‘thelinuxchoice.’ It hacks social media and related platforms. Once again, with ngrok, you can skip the hosting or port forwarding services.
This tool is gaining slow popularity with youngsters. And is best suited for data harvesting through WAN (Wide Area Network). Yet, the only con with Shellphish is that it cannot bypass the 2FA.
Highlights
- 18 general + 1 custom website.
- BASH language [Bourne-Again SHell].
- Easiest setup and installation.
- Strong Copyleft, GPL-3.0 License.
Give a try on these phishing tools and experience this phishing simulation software.
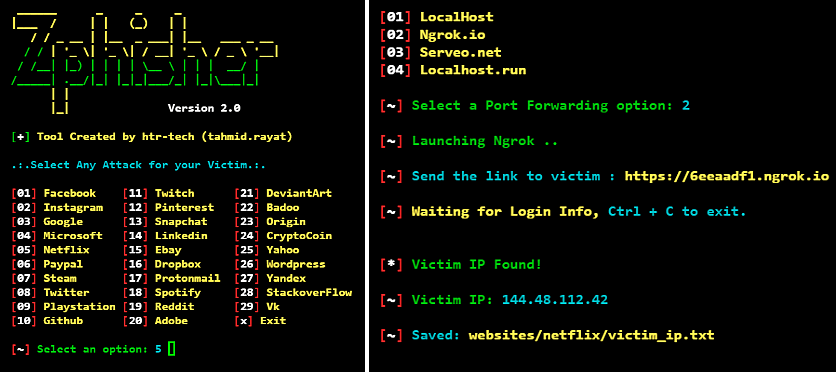
Zphisher
Did you know that Zphisher is an upgraded form of Shellphish? Yes. As one of the rarest phishing simulation tools so far, amateurs can utilize the best here, owing to its ease of usage and learnability. Indeed, you can even use this tool for generating an unlimited followers page.
However, you require multiple dependency packages, plus you need to update your pre-installed packages. And you are all set to hack 30+ sites.
Highlights
- 4 Port Forwarding Tools.
- Templates for regular social media and web pages.
- Lightweight (does not take extra space).
- Docker support
Give a try on these phishing tools and experience this phishing simulation software.
Conclusion
To this end, we would like to share the reality that there might be several other phishing simulation software programs online. But the takeaway is to use them only for educational purposes and stay ethical to yourself and your people. Rather than victimizing the general users, learn and get educated with these phishing tools. Stay secure and know how not to become a victim for another phisher shortly!
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.




 Thanks, William…
Thanks, William…



