

A framework that is used for developing, implementing, monitoring, and improving IT governance is called as COBIT framework (Control Objectives for Information and Related Technology). It was published by Information Systems Audit and Control Association (ISACA) and IT Governance Institute (ITGI) in 1996. It is the typical framework that is used to achieve Sarbanes-Oxley Act (SOX) compliance in the United States.
It acts as the common language for IT professionals, executives, auditors and senior management to understand the IT controls, management, goals, challenges, solutions and results. With this framework, communication and understanding about IT governance will become simple for the enterprise and the auditors.
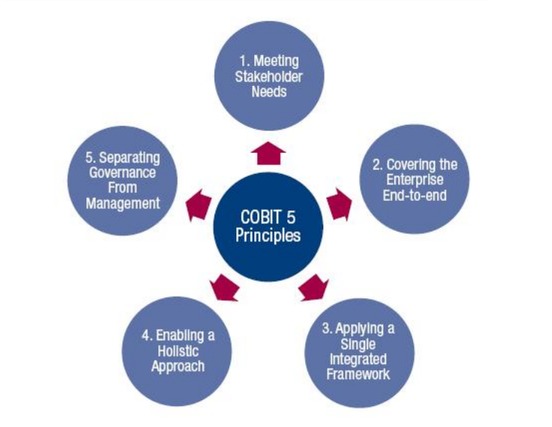
It is composed of five principles,

It is composed of four main components,
Introduction and methodology: Guidelines and scores to measure the IT governance and management of an enterprise.
Governance and objectives: Models to measure and evaluate the efficiency and success rate of 40 objectives using metrics.
Designing an Information and Technology Governance Solution: How to acclimate governance to achieve the enterprise’s demands.
Implementing and Optimizing an Information Technology Governance Solution: Steps to use the framework and design guide together.
Anybody who works on the data and information security roles like CIO, CISO, Security analysts, Director/Manager/Co-coordinator of cybersecurity, Director/Manager of Governance, Information and Security analysts, Security auditors, and more should be aware of this COBIT framework and keep themselves updated with it to keep things in order with their enterprise.
Subscribe to ‘The Cybersecurity Times’, for daily alerts on cyber events. You can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…