

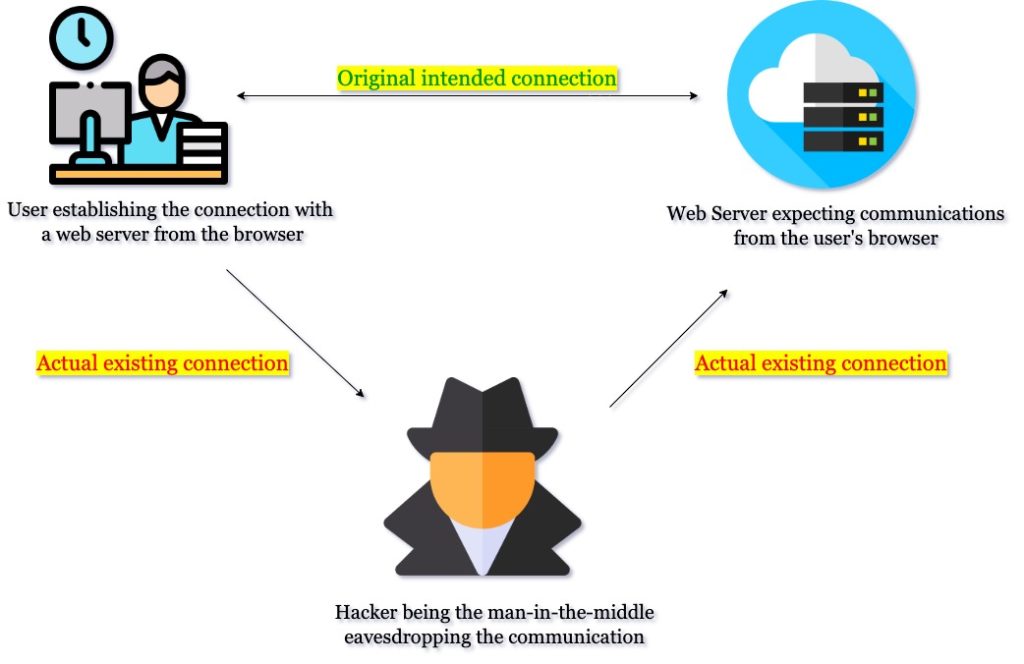
When an attacker interrupts communication between two different entities in an attempt to eavesdrop the conversation, alter the information that is being communicated, spy on the entities or steal login credentials is called as man-in-the-middle attack (MITM). Though a robust encryption can make a difference, man-in-the-middle attacks are impossible to detect, as the attackers can redirect the traffic to phishing sites or to the actual destination to keep their interruption invisible.
A random user may receive an e-mail which appears to be from his bank, which would have a link to the bank website and once he clicks it, then the browser navigates him to a specially crafted legitimate looking bank site. If the user enters his credentials and logs in, then the attacker would have captured the credentials and redirect the traffic to the original bank website bringing no doubt to the user. In this example, the attacker has employed both phishing and man-in-the-middle attack to execute this hacking operation.
Man-in-the-middle attacks happen in two stages, Interception and Decryption. Also, they can be through physical proximity or virtual means using a interception tool. Attackers are always looking for a weak network or they create an artificial network, which could lure users to make them fall victim for the bait. An attacker could identify a weak WiFi network in public places like restaurants, bus stations or airports, and then he could compromise the network by breaching the passwords and eavesdrop on the users that connect to the network. They can do this either by either breaching the password using brute force attack or they can use interception tools which they can deploy to interrupt and eavesdrop on the communication between the connected entities.

Attackers can eavesdrop and decrypt devices in many ways. Below are the seven unique ways through which they can achieve it.
Attackers will create bogus WiFis which would look legitimate like the brands and stores nearby. For instance, an attacker could sit next to a McDonald’s and set up a WiFI named ‘McDonald’ making the customer of the store connect to it, he could also leave this WiFI open for more connections. Once the users connect to the network, the attacker could easily read their credentials, payment card information and more. He could even record the details for a different motive.
When a browser connects to a HTTPS website, it means that the site is secured by ‘Secured Socket Layer’ and users will feel little secured browsing it. In case of HTTP the connection can be interrupted and thus users avoid visiting these sites. SSL is the different, which encrypts the communication between the browser and web server. An attacker could hijack the SSL connection and intercept the original connection from a different browser and server, thus reading the information from the user’s browser and the server.
Attackers can trick users believing that they had connected to a website or a person by spoofing the IP address. Attackers can impersonate a person or website and lure the targets through faking the IP addresses, which in other terms called IP Spoofing.
A technique that forces the users to a website which looks like a legitimate site and lures the users to interact with the site by spoofing the Domain Name Server is called as the DNS Spoofing. This is a type of man-in-the-middle attack as it can read user’s interaction with that bogus website which the attacker has created himself.
Websites with HTTPS in the url are found to be secured and that’s the reason most of the users do view those sites without any hesitation but unfortunately attackers can make users land in a fraudulent website with the same HTTPS but with their control. They could intercept and decrypt the information that is being exchanged by the user on that website. This type of man-in-the-middle attack is called HTTPS spoofing.
Attackers could compromise any official e-mail accounts of organizations and read the confidential email conversation or broadcast emails to the recipients. To illustrate, assume attackers had breached into bank’s e-mail account, they can now ask the customers to share any information they want and this could eventually lead to customers losing money to attackers who impersonated the bank itself. The worst part is that the customer would not even know they had been cheated.
Cookies are a small piece of information that is stored in a computer by the browser for using it on later occasions. With cookies users’ browsing experience could be swift and simple, however hackers could steal these cookies and use the information for their own benefit. MITM attacks also include stealing of cookies which is the hot spot for login credentials, addresses, payment card details and more.
MITM attacks may not have cause immediate chaos but they are stealthy and can continue attacking your communication if not detected. Hence users and enterprises need to secure their communication proactively to avoid any anonymous interceptions. Please follow the below steps to stay immune against MITM attacks,
Man-in-the-middle attacks are one of the oldest forms of cyberattacks, and even these could be fatal if not detected and dealt with. Robust cybersecurity strategies, with right tools and talents could be beneficial.
Subscribe to ‘The Cybersecurity Times’, for daily alerts on cyber events. You can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…