What is Phishing?

The process of gathering sensitive information or deploying malicious programs using deceptive e-mails and websites is called Phishing. This is an ancient type of cyberattack that is being used by hackers to lure the targets to achieve their goal. It is often the most common means of cyberattack which is used primarily to breach into a network or system. It can further be used for other cyberattacks like malware deployment, encryption and more.
According to Verizon’s Data Breach Investigations Report, one third of cyberattacks do involve phishing. The attackers frame the subject line in such a way that the recipient would believe that it is actually from an entity they are connected with or aware of.
Why is phishing so common?
Cyberattacks are very sneaky and attackers need to craft in a perfect way for a successful deployment of it. However, unlike other attacks this is not very complicated and does not require any vulnerability in the network for its deployment. It’s completely independent, depends on totally the execution of it and does not take a lot of time to create one. Here’s an article that explains ‘How to produce a phishing attack in 5 minutes‘.
Users aren’t always cyber aware and accidentally or intentionally open a phished e-mail, click the links in it or download anonymous attachments. Attackers will actually increase the belief toward their e-mail in such a way that the open rates would be high.
For instance, they can create an e-mail which is with a subject line related to a bank name, e-commerce site, or from the government itself. These attacks are so easy to deploy because of its simplicity and a phishing kit which can simplify the overall process of it. Users can also verify about the attacks that are related to brand exploitation at isitphishing.ai
What is a phishing kit?
A package of tools and website resources that are combined together installed in a server to facilitate the hackers in deploying the campaigns. Once it is installed, all the hackers have to do is to create some targeted content and deploy the deceptive e-mails to the selected audience. These kits are easily available in the Dark Web at hackers reach. While these kits can ease the entire hacking process, certain kits can be hackers the sophistication of deceptiveness by providing a reliable picture of brands. In Akamai’s research paper titled ‘Phishing-Baiting the hook‘ report different variants of the leading brands like Paypal, Microsoft, Dropbox and DHL were found.
Anatomy of a phishing kit
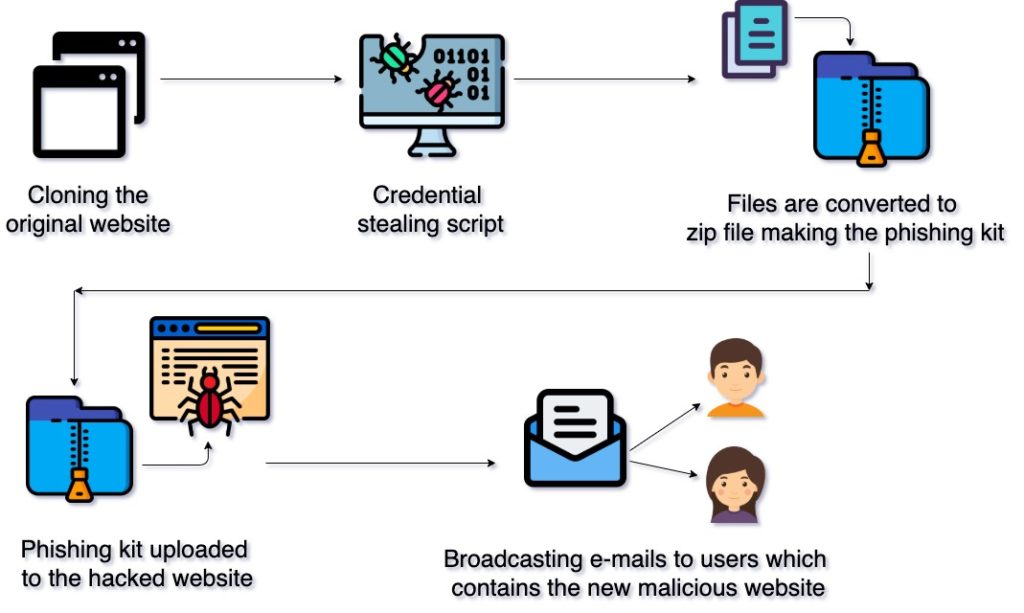
Types of phishing
There are two main types, with two main motives, access to sensitive data and deploying malware through malicious documents. The types are,
- Spear Phishing– Specially crafted attack at a targeted individual
- Whale Phishing or Whaling– Specially crafted attack at C level individuals like CEO, CIO, CISO, CTO; etc.
How to identify phishing?
The best way to identify it is to understand how attackers have used it in the past, by studying the examples in the wild users can understand the pattern in the cyberattacks that has been executed. Most of the bogus e-mails comes with either of the one mention below which would blow of its cover,
- Urgent e-mails that you weren’t looking forward to.
- Fear, Anxiety, Excitement targeted e-mails.
- Spelling mistakes in the content.
- Improper or fake domain name of the entity.
- Unknown sender with unexpected request.
- Click bait file names like Bank Statement, Won a Cash Prize, etc.
- Weird way of a login page reloading event after you have typed in your credentials correctly.
- Weird links in the mail, that is pushing to be clicked and read.
Below are some very commonly used malicious intent subject lines,

How to mitigate against it?
Enterprises can follow the below steps to combat against these attacks proactively,
- Employe e-mail security management procedures to restrict and block mails from unknown or third party source based on your company policy.
- Sandboxing could restrain users from clicking malicious links in the mails.
- Practices cyber awareness, occasionally conduct drills and reward the most cyber aware employee.
- Employ browser security policies like restricting download of attachments, blacklisting and whitelisting websites.
It is the most common hacking methodology for hackers, a successful combat against this attack could keep the attackers at the bay.
Subscribe to ‘The Cybersecurity Times’, for daily alerts on cyber events. You can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.








