

The CISA has alerted the IT community for a critical Java deserialization vulnerability affecting several Zoho ManageEngine solutions. The security flaw CVE-2022-35405 can be exploited without user interactions and perform remote code execution on devices that has the following Zoho ManageEngine products – PAM360, Password Manager Pro and Access Manager Plus.
The POC and a Metasploit module is disclosed since August for gaining RCE as the user. ManageEngine already warned its customers about the exploit in July.

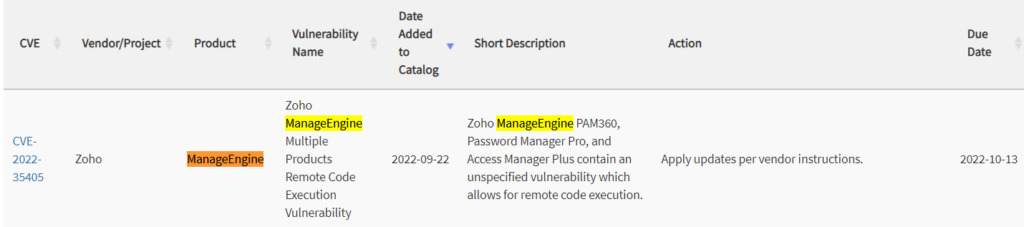
CISA also did add this Zoho ManageEngine vulnerability to the known exploited vulnerabilities catalog, and ensured all the federal bodies are aware of it and patching the same.
The entities have until Oct 13th to ensure their networks are patched against those exploits.
The US Cybersecurity agency has strongly requested organizations across the nation to prioritize patching the exploit.
Since these types of exploits are the usual loophole for most cybersecurity incidents, the CISA is keen on ensuring the importance of patching them.
CISA has now added 800+ vulnerabilities to the list originally published, IT professionals and admins are requested to keep track of the exploits and patch them as soon as possible.
Zoho ManageEnginne vulnerability is big as the vendor solution is widely used across geos including North American Region, and in recent times ManageEngine servers are constantly targeted with Desktop Central a.k.a Endpoint Central in particular.
Previously the tool was breached and the data associated with it was sold on hacker forums in July 2020.
APT27 hackers were the ones behind the breach, FBI and CISA released security advisories regarding the Zoho ManageEngine vulnerability that allowed dropping web shells on the networks of corporate network including healthcare, financial services, IT consulting and electronics industries.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
Recast Software offers a suite of tools designed to enhance and simplify endpoint management in…
Patch My PC is a widely-used solution that simplifies third-party application management by automating app…
Explore the top 5 best Microsoft Intune alternatives, comparing key features, user reviews, and capabilities…
Discover the top 7 smartphones of 2024 with best security features, offering privacy, performance, and…
Discover the top 11 log management tools for efficient system management and monitoring. Learn about…
Explore the top 5 threat intelligence tools, their features, and how they enhance cybersecurity against…